In-Depth Survey of Digital Ad Technologies, an in-depth study of digital advertising technology
In-Depth Survey of Digital Advertising Technologies(Translated by Gu Mingyi,The new marketing media is authorized to be published)
Introduction to Translators:
Lead Researcher, WFAP2025 Future Advertising Program,
Associate Professor, MBA Chinese University, Shanghai University,
Visiting Scholar, Department of Advertising, MSU Michigan State University
Visiting Scholar, Wharton School of the University of Pennsylvania
He has served as executive director of interactive media in a business circle, chief scientist of outdoor data, member of the growth committee of AAA American Advertising Association, member of the Academic Committee of the China-Guangzhou Association/expert of the Internet Committee, and vice chairman of the board of directors of the China Youth Brand Scholars Forum, and was awarded the Outstanding Young Scholar of China's Digital Marketing Decade.
Overseas Coordinator Launches THESD (Shanghai), 2018 First International Conference on Intelligent Science and Advertising Development;
Convenor of the Smart Advertising Sub-Forum of the 2019 American Advertising Institute Global Annual Meeting (Peking University) and published the China Smart Advertising Model and User Data Privacy Protection Policy and The Models on Synergy of Branding and Selling (Synergy Synergy: Branding in the Digital Age)
Frontier brand theorists, experts in scene data research, intelligent brand communication and user data asset right innovators.
In-depth Research on Digital Advertising Technology
Professor John Koppland's team,Georgia Institute of Technology, Department of Electronics and Computer Engineering, Atlanta
(Full text of about 33,000 words, reading takes 15 minutes)
Gong Chen,Department of Electrical and Computer Engineering, Georgia Institute of Technology, Atlanta, GA
Jacob H.Cox, Jr., Department of Electrical and Computer Engineering, Georgia Institute of Technology, Atlanta, GA
Selcuk Uluagac, Department of Electrical and Computer Engineering, Florida International University, Miami, FL
John A. Copeland, Department of Electrical and Computer Engineering, Georgia Institute of Technology, Atlanta, GA
https://ieeexplore.ieee.org/document/7390161
Summary:
In factSome of the world's most famousITCompanies are advertising companies that earn major revenue from digital advertising.For digital advertising reasons, theseITGiants are able to continuously advance information technology in ways that improve our daily lives. The benefits of this relationship include having powerful search engines and mobile apps for freeWebBrowser. Nevertheless, it turns out that“Free.”is through our interactions in the digital advertising ecosysteminteractionsto pay for it. Digital advertising is not without challenges. The problem stems from the support usedWeband a complex platform for advertising on the mobile app interface. This is especially true for ad links. In addition, with the development of new methods of advertising development, it is also possible to affect the good or bad of its basic ecosystem. Researchers are interested in understanding the ecosystem, the factors that affect it, and strategies to improve it.
This surveyThe main contribution is that it is the first review of the digital advertising ecosystembecause it is suitable for online websites and mobile applications. In the process, we will explain the digital advertising relationships in this ecosystem and their technical, social, political, and physical impact. In addition, explore alternatives to advertising principles and other legal and malicious advertising methods to compare and contrast competitive digital advertising technologies.
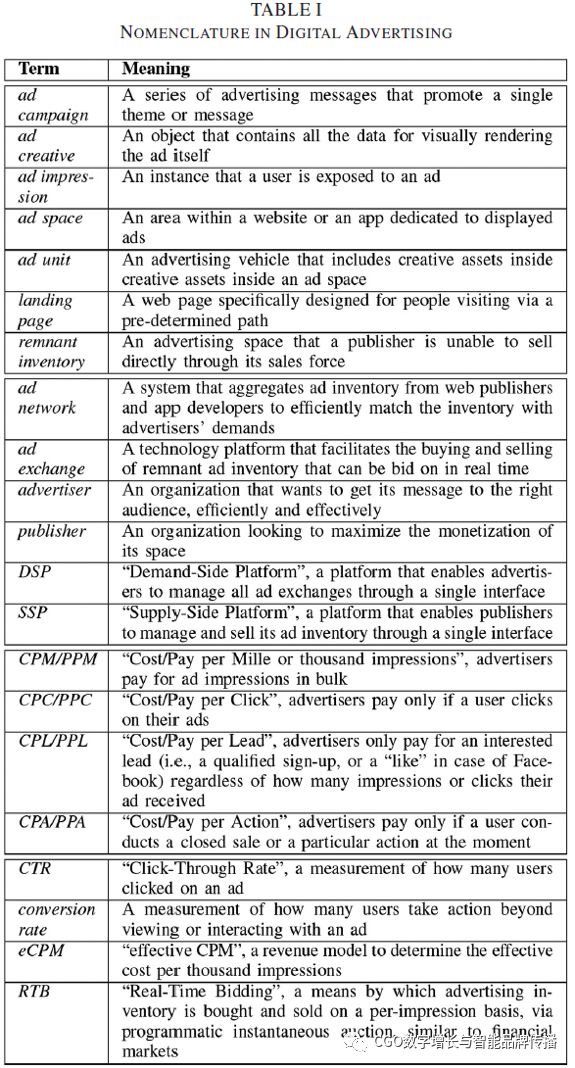
Keywords:Digital advertising, mobile advertising, online advertising, monaization, networking, privacy, security, advertising networks, advertising policies.
SECTION I.
Introduction
Digital advertising (e.g., Internet advertising), including online and mobile advertising, is the driving force of the monetization of the Internet as a whole. Although since20Century.80Online advertising has been changing the rules of the industry since then, but relatively new app mobile advertising has taken its place in the mobile phone market. Together, these platforms are driving advertising revenue to an all-time high. According to the Interactive Advertising BureauIAB2014Internet advertising revenue increased year-on-year in the first and third quarters of the year17%[1],[2]。 These reports are also specified separately116billions of dollars and124$100 million in quarterly earnings. While the growth of Internet advertising has been impressive, it has come from2012Year ($10.1 billionto2013Year (193billions of dollars), global mobile advertising revenue achieved92% of the huge growth.GartnerFurther predictions2013to2016the year will increase again100%。 This huge potential for revenue creation makes digital advertising a major driver of networking and mobile technologies.
Today, U.S. digital advertising revenue reached $104 billion, accounting for 51.5 percent of total ad revenue of $202 billion (MANGA, 2018), while China's digital advertising revenue accounted for more than 53 percent.
For example, consumers are now exposed to displays directly on their devicesHTML5Rich media advertising (short for).“Advertising.”)。 Keeping pace with this technology, cellular networks are upgrading their infrastructure to support additional overhead. Of course, this will ultimately improve the customer experience when browsing the site or using mobile apps“APP”)。 In addition, advertising technology is driving political legislation aimed at protecting users' privacy. For example, the Federal Trade CommissionFTCand submitted by the Attorney General of the State of California2013annual report[3], calling for restrictions on cross-application tracking by application developers using data collection and storage. The same report also recommends that application developers cancel access to global device identifiers, or mobile device identification numbers. Similarly, developers are called in to encrypt data, restrict access to user information, and use special notifications to draw attention to application privacy settings. Other privacy practices, such as explaining how to collect and use the user's personally identifiable information (PII), has been enforced in some U.S. states and Europe[3]。
From a high level of observation, ad brokers basically work with advertisers to deliver ads that they are willing to accepthoston their websites and mobile apps. Mobile advertising can take the form of mobile video and TV, text and multimedia messages, mobile networks and many applications. Our list is more exclusiveexclusive。 Given the growing importance of mobile advertising, in this survey we focus on online and in-app ads displayed on mobile devices. In addition, in order to provide timely and mobile ad status-related surveys, we limit the scope of this survey to2007to2016technical papers published in 2000 and recent articles on relevant websites. In addition, we compare in-app mobile ads with web-based ads to reveal basic statistics that mobile advertising researchers, professionals, and skilled amateurs might be interested in. The survey also introduces a number of terms, which are listed in the table for the convenience of the readerI.
The following contributions are made in this report:1.The first technical survey report related to online and mobile advertising.
2.The algorithms related to digital advertising are discussed.
3.Online and mobile advertising roles stand in stark contrast.
4.Comparing the advertising research and development goals of academia and industry.
As shown in Figure 1, the rest of the survey is structured as follows.
The second part provides the background of digital advertising, including basic concepts and basic statistics。
In the third part, we identified the main monecurations used in digital advertisingmonetizationMethod.
The fourth part introduces the network scheme inherent in the advertising ecosystem.
The fifth part solves the user's privacy problem and the advertiser's goal.
The sixth part analyzes all kinds of malware and countermeasures that affect digital advertising today.
The seventh part introduces the human factors that guide the research of advertising.
Part VIII highlights the energy and data limitations of mobile devices and their relevance to online and mobile advertising.
Finally, in Part 9, other points of interest in the survey are discussed, followed by conclusions in section 10.
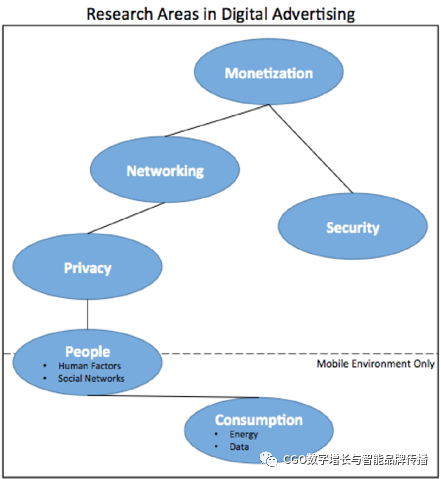
Figure.1 The structure of the paper
SECTION II.
Background
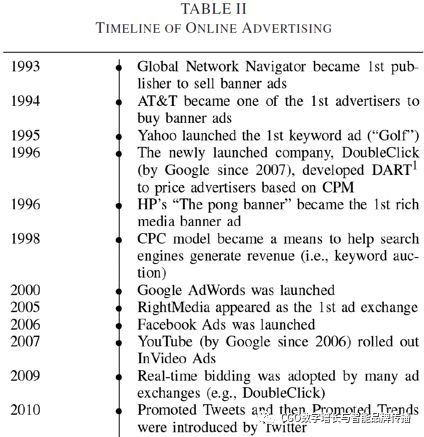
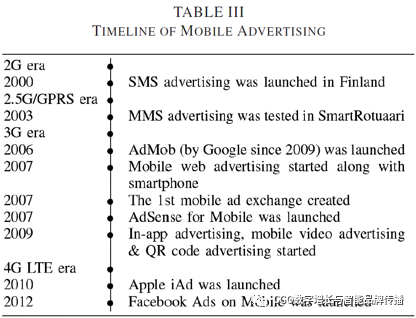
Digital advertising is a relatively new form of marketingspread rapidly throughout the Internet. As online and mobile platforms provide marketers with more access to customers, they have also undergone many technological, policy, and security changes. For historical background, the tableIIand tablesIIIProvide timelines that describe notable milestones in online and mobile ads, respectively.
Digital advertising systems include a series infrastructure that allows users, publishers and advertisers to interact with advertisers in the advertising ecosystem. Although publishers provide ad space on their sites, advertisers pay to place ads on those sites. Therefore, collaboration between publishers and advertisers is required. While some large advertisers can negotiate directly with a small number of large publishers, as traditional billboards and paper media do, this direct collaboration is not suitable for the large number of publishers and advertisers on the Internet today. Advertising brokers, including ad networks (referred to as“Ad networkAd network”and advertising transactions (short for short).“Ad exchangeAdx”Represents multiple agents. Although the ad network is essentially somewhere between publishers and advertisers, the ad trading platform provides auctions for advertising space between various entities, including ad networks, supply-side platforms, and demand-side platforms. Therefore, when users view multiple ads on a web page, they may appear from multiple sources, as shown in the figure2shown.
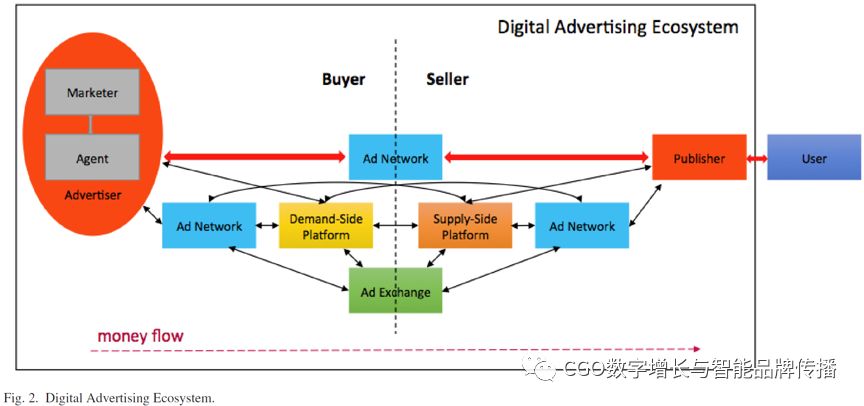
A.Online advertising ecosystem Ecosystem for Online Advertising
Figure.2The path highlighted in red represents a simple model that is widely used in academia.In this diagram, the advertiser represents the source of the currency, and the user acts as the initiator of the action. However, the user must initiate all actions with the publisher (or application provided by the application developer). An ad network is an entity that connects everyone. Similarly, a red line represents the simplest path with the fewest hops between advertisers and users. However, the advertising ecosystem is not that simple. Other entities also exist in the model, as shown by several other arrows that show various interactions. For exampleDSPUsed to aggregate multiple advertisers, andSSPAggregate multiple publishers. In addition, the advertising exchange is similar to the New York Stock Exchange because it brings together all buyers and sellers. These entities are further subdivided into buyers and sellers. Buyers include publishers,SSPand advertising networks, while sellers include advertisers,DSPand other advertising networks. Please note that both ad networks and ad transactions assume both roles. In addition, in this hybrid ecosystem, all paths from advertisers to users are possible. The currency flow is displayed with a single arrow, while the information flow is represented by a double arrow.
It is undeniable that ad networks typically use different servers (i.e., publisher ad servers and advertiser ad servers) to manage publishers and advertisers separately; There are two types of publishers, including1by the ad network (e.g.,GoogleSearch orFacebookPublishers who own and operate, as well2Co-publishers that are not managed by the ad network (for example,redditOr.TechCrunch)[4]。 These co-publishers can be subject to their service level agreementsSLAA constrained premium publisher, or self-service publisher, can sign up for an ad network at any time. We focus on more general cases, including self-service publishers. For these publishers, ads must be obtained from the ad networkIDand the appropriate source code, and place it in the publisher's source code to display ad impressions on the publisher's website.
GIT researchers discuss the path of building an online advertising ecosystem from the perspective of technical experts, and refer to a very small number of traditional advertising industry knowledge systems, the entire technology path is based on the idea of the Internet industry (Google/Facebook/Amazon) to become centralized.
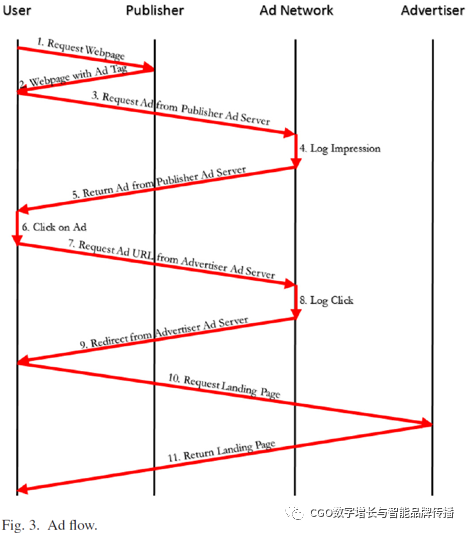
After explaining how ad impressions can be merged with self-service publishers' websites, we'll now look at how it happens when potential customers click on ad impressions. In the figure3, which describes the steps of the process. When the user starts loading the page (step.)1And.2), the ad exposure is requested by an algorithm that exists in the web source code of the ad network server (step3)。 Ads that identify publishers assigned by the ad networkIDThe ad network's server then records the request (step).4), apply rules previously established with its advertisers, and return ads that include unique identifiers for click tracking (steps).5)。 Once the user clicks on the ad (step.)6), that will beHTTP GETThe request is sent to the ad network (steps.)7)。 This is treated as a click event by the ad network and is logged for billing purposes (steps).8)。 Then, the ad network passesHTTP 302The status code redirects the browser to the login page of the advertiser passing through the client (steps9)。 Landing pages are hosted directly on advertisers' ad servers or on content distribution networks (CDN)3on. Once this is reached, users are now able to browse the items (steps) on the sign-in page10And.11)。 Under.Wangand so on[5]For distributed network architectures (for example,AOL/Akamai:87Milliseconds and Google:122milliseconds), the content delivery of online ads may take about100Milliseconds, for stand-alone servers, is approximately required200milliseconds (for example,Adblade:207milliseconds).
Typically, when an ad network first encounters a user, it sends it to the usercookieor use other indirect methods (for example,IPAddress andHTTPuser agent combination). The ad network can then do itAPIcalled or with the userHTTPResponse. As a result, ad networks can tag network users, determine their browsing patterns, and measure the effectiveness of specific ad campaigns.
You must sell any empty ad space to advertisers for a limited time(For example,DoubleClickAd ExchangeFor.100milliseconds); To maximize potential revenue across the ecosystem, multiple ad networks have formalized partnerships that include predefined revenue sharing. When needed, the ad network will ask each partner to fill it out. However, the method is still very inefficient. Therefore, the ad exchange (for exampleGoogleof theDoubleClickAnd.Yahoo!of theRightMediaSolve this problem by loosely aggregating all platforms together. Based on real-time bids (RTB), ad trading platforms are able to perform large-scale aggregations and enable single ad space bids, resulting in higher revenue for publishers and ad networks, while providing advertisers with fine granularityfine grainedAdvertising bit bidding. In order to complete an ad request, the user must initiate at least four consecutive requests, as shown3Shown: First, the publisher's ad server, the second is the ad trading platform, the third is the winning advertiser's ad server, and finallyCDN。
With the development of advertising transactions, there are new problems from auction to optimization[6]。 Issues include a fixed percentage allocation plan and intense competition from the competitive market[7]。 In practice, however, the focus of ad exchange is still very similar to the problems in the ad network. Perhaps these issues are not yet fully identified, as ad exchanges still have very few large data sets. For example, by inRightMediaAd logs that use the ad network,Stone-Grosset al[8]Ability to find suspicious publishers, primarily through the use of local traffic and personal detection. However, they are unable to detect overall fraudulent activity across the platform.
On a larger scale,RTBAuction model based on second price. As a result, publishers are compensated for the second-highest bid paid by the winning advertiser. To support this phase and verify the integrity of the auction,VEX[9]Each Spot Advertiser is required to initiate a three-way communication in an advertising transaction. While doing so,VEXReasonable latency and processing costs can still be achieved.
B. Mobile Advertising Ecosystem for Mobile Advertising
According to the literature[10]Server redirects are used for the mobile ecosystem to accommodate slower connections and limited data usage, compared to online ads that use client-side redirects for ad networks. In addition, unlike online advertising, mobile advertising merges with apps on mobile devices. As a result, this form of advertising can provide advertisers with a unique way to interact with users and their personal information. We're now talking about platforms and libraries available to mobile app designers to find ways to monetize their apps through in-app advertising.
1Mobile platform
Under.Gartner[11]the statement thatAndroidAnd.iOSIt is the world's two most popular smartphone platforms. Although.AndroidAnd.iOSThe platform attracts third-party developers to create mobile applications, but all of these applications must be run as non-privileged users in a sandbox application execution environment. In addition, developers may experience limited memory on all mobile platforms. For example, inWindowsPhone, allowing the application to consume no more than at runtime90MBof theRAM[12]。 In addition, smartphones contain sensors (e.g.,GPS, accelerometers, gyroscopes, magnetometers, photonometers, microphones, cameras and speakers). Therefore, the licensing system is used to program interfaces through applications (APICall to control access to system resources.
Application permissions can be granted in one of two ways:1Use time and2Installation time. The former is iniOSAnd.WebUsed in the browser, requiring the user to trigger privileges in the applicationAPIPermission to approve or deny resources (for example, location) when called.AndroidThe latter used prompts the user to approve the hazard permissions listed in the manifest file before installing the application. These dangerous permissions (for example,RECORD_AUDIOYou can access private user data or control your device. Unfortunately, permission authorization during installation is all or all. This means that the user must grant access to the requested user-owned resources or terminate the installation during the installation.
"Recording rights" undermine privacy issues, and lawmakers are asking them at Zuckerberg's congressional hearing in 2018Facebook。There are now high-level concerns, including the EU GDPR General Data Protection Regulation (2018), China's Cyber Security Act (2017), the Digital Security Regulation (2018) and a series of other regulations, the California CCPA California Consumer Privacy Act (effective 2020) are strengthening regulations.
AndroidThe application lacks a single entry point, such asmain( ) and consists of one or more application components (i.e. activities, services, content providers, and broadcast receivers) through which they interact with the system[13]。 When the privileged application is in placeAPIPermission re-authorization also occurs when a component runs transparently in the background when it is called[14]。 Unique for each applicationAndroid UIDAssociated with its permission list (in the application).AndroidManifest.xmlspecified in the file). These system permissions can be divided into4level of protection (i.e. normal, hazardous, signature, signature or system)[15]。 In general, application developers must adhere to the principle of minimum permissions during application development. ButStowaway[16]Still thereAndroidExcessive privilege issues (i.e., unnecessary permissions are required) are identified in the application. As a counter,PScout [17]Use static analysis to reveal unnecessary use of non-system permissions in a few cases.Quire [18]Allows applications to communicate between processes by tracking (IPCCall the chain to adjust its permissions.
For.iOS, only third-party applications are allowed to use the public framework. Any privateAPIuse will result inAppleDirect rejection during the audit process, which requires all executable code to be usedAppleThe certificate issued is signed. The review process is said to be very secure, but an attacker can still achieve malicious activity by building a new execution path after the application audit process[19]or inject malware through a malicious charger[20]。
2Advertising library
AndroidAnd.iOSThe groundbreaking discussion of mobile advertising in China may be attributed to each otherTaintDroid[21]And.PiOS [22]。TaintDroidHalf of its research applications were found to share location information with third-party ad servers in clear text or binary format without the user's consent. Similarly, through1.1KBest-selling freeAndroidApplication research,Encket al[23]Confirm advertising and analytics (short).“A&A”The service is willing to explore licensing and obtain other key information, such as the identity of the user's mobile phone as an international mobile deviceIMEI。 As for.iOS,PiOSpointed out that because of its embeddedA&Alibrary, more than half of the research applications that cause the leak of unique device identifiersUDID。 Although.Egeleet al[22]Forecast onlyAdMobCollected40Byte identifier associated with Google account, Smith[24]confirmed that many apps are collecting Amazon,FacebookAnd./Or.Twitterof theUDIDAnd login information, they are able to track users in real time and reveal their usage patterns. When with long-term trackingcookieor time-stampedIPWhen the address is used in combination, the user's location information and other private data will be handed over and registered. In a follow-up study,Smith[25]Also claimed millionsUDIDLeaked to application developers and even hackers. SameSmith[25]Pointed out.iAdBanners are also collected and will beUDIDTransfer toApple。
To get sustained revenue from apps, many mobile app developers consider mobile advertising. For exampleFlurryIndependent“Angry Birds”to collect and upload statistics to remote servers to download and present ads during the game[26]。 Developers register their financial information[27]and its application metadata, including application name, category, requested permissions, app store links, average rating and downloads[12]。 In turn, developers receive an identifier and a software development kit (SDK)。SDKProvides developers with a library to use their ads ( short for short).“Ad library”and provide abstractions for the complex extraction and reporting protocols required by the ad network. Therefore, the library can be usedWebViewto facilitate ad loading;WebViewis used inJavaScriptInterfaces can cause attacks on malicious Web pages or other applications[28]。
There are many other vulnerabilities to user privacy[29]。 In the paper we surveyed, we reported the number of ad libraries implanted in each application, with one researcher's results different from lying next. Although most applications bundle multiple ad libraries[23],[30]But the researchers[31]claimed more than75%32KThe app has only one ad library bundled, about that1% bundles more than five ad libraries. Ad libraries allow ad servers to properly allocate ad revenue by tracking clicks from the unique click URL associated with each ad impression[32]。 In.Android, requires the developer to be inAndroidPackage Kit(APKcontains the permissions required for the ad library. Because all permissions used by the application are storedAndroidManifest.xmlfile, so the ad network can access the same services as the host application. Each ad library may require different permissions, but alwaysINTERNETPermissions.[33]。
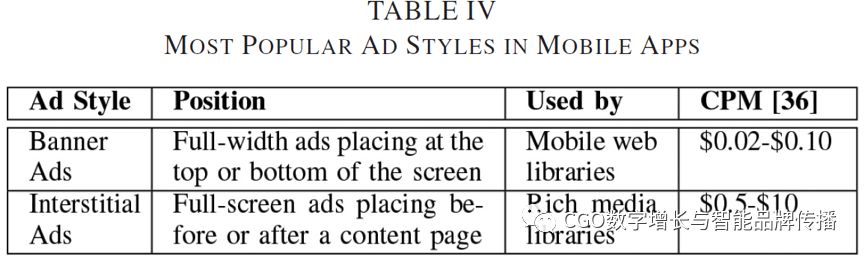
Mobile advertising is used not only to promote external brands, but also to promote applications in the market[34]and they are usually embedded in banners and intersted ads[35], such as a tableIVlisted. Static ads are up to the size15KB;However, the average size of these ads is different1.5KBTo.5KBbetween uploads and downloads[12]。 In addition to banner ads and intersted ads,AndroidThere are also notification ads (for example,AirPush,MobPartnerAnd.SendDroidand icon ads (for example,EverBadgeAnd.AirPush)。 As the name implies, one appears in the notification area of the application and the other appears as a shortcut on the app's home screen. Of course, for understandable reasons, neither method of advertising is popular. They are mainly in violationGoogledeveloper content policy. Second, they have a negative impact on user satisfaction. For ad libraries, they can be divided into three groups[27]:1Mobile network library,2Rich media4Library3Advertising media5。 Although the latter uses traditional web technologies to request, deliver, and display banner and intersted ads, the first two groups doHTML5to create video ads. Because mobile app developers may be bundled with multiple ad libraries, ad mediators (for example,AdWhirl,MobClixAnd.Burstly [35]has appeared to coordinate the various ad libraries in the app. In addition, they query the subscription network for ads based on factors such as the developer's percentage allocation of ads. Today, most ad networks offer mediation options. For exampleAdMobAllowed with16other ad networks (for example,Adfonic,Flurry,InMobi,iAd,Jumptap,MillennialMediamediation. The introduction of these mediation services may increase developer revenue, and in cases where one ad network is unable to present ads, another ad network can fill the space.
The popularity of an ad library can be achieved by the number of applications that use the library or by including libraries[33]The number of application installations is calculated. though before10name, before25name and front33The advertising library occupies the app installation separately[71]of the71%,90% and95% market share, howeverAdMoband the othersGoogleAdvertising and analytics services are the sameAndroidSystem.2010YearsAdMobfor the global over15,000mobile sites and apps to advertise[37]。 in the studyGoogle Playof the55KAfter the free app,Tongaonkaret al[38]show, near12KApps bundle the most popular ad libraries (that isGoogleads). SameGraceet al.[27]revealed, inAndroidIn the app,Googleof theAdMob,AdSenseAnd.AnalyticsThe network is listed100the top five in a comparable library. FlurryAnd.MillennialMediaIt's the other two libraries in the top five.
In a study[35]During the one-day main European mobile operator network traffic tracking period, found about4.5%AndroidAnd.iOSThe user has clicked at least onceAdMobAdvertising. Presumably,AndroidAnd.iOSmore than two-thirds of the ad traffic withAdMobcorresponding. More generallyiPadon the deviceAdMob。 On these devices,AdMoboverAppleOwned ad library (i.e.iAd), the market share exceeds90%[35]。 Because of its ubiquitousity,AdMobIt is often used by researchers in case studies. Import.AdMobAfter the developer passes inXMLDeclared in the layoutAdViewOr willAdViewThe instance inserts the view hierarchy directly to handle the layout[39]。 In order to request ad content, the ad library firesAdRequestAnd inAdViewload ads in[40]。 With other ad libraries (for exampleAirPushIt's the same.AdMobit's confusingAPICall to protect intellectual property[27],[40]。 However, it also requires individual and clear informationGPSCoordinate.[29]。 These mobile ad interactions are primarily by usingREST APIPlain textHTTP GETRequest to complete[35]。 Upon receipt of the request,AdMoball will be mediated internallyGoogleAdvertising services (for exampleDoubleClickAnd.AdSense)。 Of course, other ad networks can use different protocols. For exampleInMobiSend one per adHTTP POSTRequestMillennialMediaBuild twoHTTPconnection to get ads and related static content from different servers[35]。
SECTION III.
MonecuringMonetization
Typically, there are two types of ads in digital ads (i.e., display ads and search ads) and four pricing models (i.e.,CPM,CPC,CPAAnd.CPL)。 Table.Vdescribes the relationship between ad types and pricing models. Note that un aligned lines are designed to indicate that display ads are also includedCPC/CPA/CPL。 Display ads also include content-related and behavioral ads. In addition, in the models described,CPMAnd.CPCare the two most common.
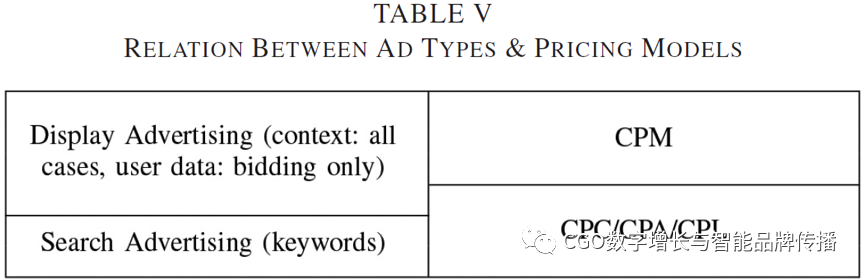
For budget purposes, many advertisers allocate budgets for their ads (or ads) to span a specified period of time. For example, category-based ads (for example, context display ads) are updated monthly (for example,Revisitors.comon the monthly5KThe click cost is28.95dollars), while keyword-based ads (for example, search ads) pay daily (for example, Google:4.5Dollar./Click and Yahoo:$ 3.0/Click)[41]。 Publishers also seek to make a profit and get advertisers to pay as much as expected70% profit. Finally, the ad network receives the remaining share of the advertiser's payment.For example, the ad network retains advertiser payments30% or so(For example,GoogleAdSenseFor.32%) and assign the rest to its publisher. In other cases, publishers must provide a certain number of conversions to collect from ad networks or advertisers (for example, smart pricing). HoweverAd networks can use the ad co-business model for arbitrage(i.e., buy cheap advertising space and resell it at a higher cost)[8]。 For exampleCriteoPay publishers for every thousand impressions and sell each conversion to advertisersCPC/CPAto mediat relationships between publishers and advertisers[42]。 At lasteCPMMetrics are used to evaluate conversion rates and overall success rates.
A. Pricing mechanisms for online advertising, Pricing Mechanisms for Online Ads
1) CPM Earnings Model Revenue Model
CPMis a relatively simple pricing model. In.CPM, the display fee (CPM(u,p,a) depends on three variables[43], the network runs (RONa), the flow quality multiplier (TQMp) and user intent (Ia(u) product:(CPM(u,p,a)=RONa×TQMp×Ia(u)。 Normal in the ad networkRONCampaignsaEvaluate the advertiser's base price (average).1.98U.S. dollars), because it is not specific to users[44]。TQMDepends on the publisherpthe potential value of the advertising space. For example, a popular publisher's ad space might require a higher rate (popular publishers are).2, the reputation of the site for0.1, the remaining publishers are1In addition, the location of your ad space is important if it falls into the typical user's web browsing habits[45]。 Additionally, the user intends to pass through the useruNetwork tracking inference (range from2To.10, but on average3.3[46],Right.CPMModel andHTTPThe data set's research shows that50%'s user intent can be accurately estimated[43]。
2Auctions
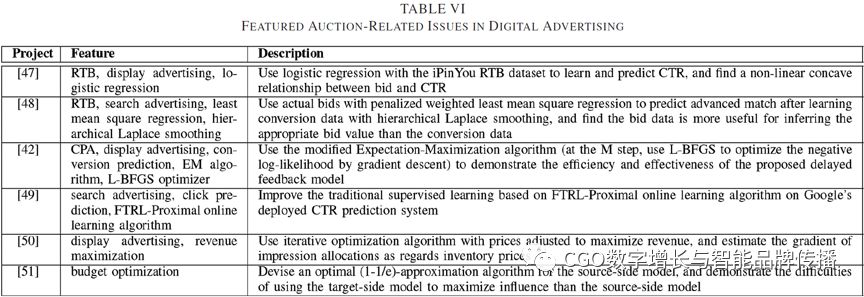
Search for ads and behavioral display ads for most of the ad space is throughRTBSold. ButRTBThere are several methods. Table.VISome of them and their descriptions are listed. Other auction features includeCPA, learn algorithms and budget optimization.
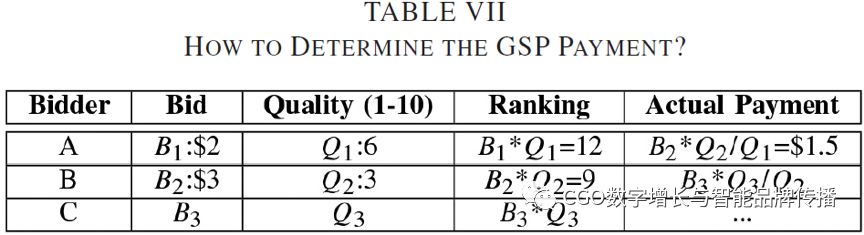
There are also various auction mechanisms for a single ad or multiple ad bids.Stavrogiannisthree different auction types were discussed[52]and includes the first price sealed bid auction and before and after the awardVickreyAuction. They found that the pre-grantVickreyAuctions are the least efficient of these models. They also found that most evaluating companies preferred a broad second price in the case of simultaneous multi-project bidding (GSPModel orVickrey-Clarke-Groves(VCGModel[53]。 For exampleGoogle,BingAnd.Yahoo!FacebookUse.VCGwhen usedGSP[48]。Edelmanet al. further evaluated the performance of these models in their work[54]They found that both models calculated advertisers based on mathematical calculations of their bids and quality scoresCPC。 When the user queriesGoogleSearch engine, search engine results page (SERPPresents relevant query results (i.e., those that closely match the user's search query) and sponsorship results (i.e., search ads)[54]。 The ads are then allocated based on the spot price of all advertisers displayed by the Spot ad. To participate in the auction, advertisers are required to submit ad codes that are bids associated with each ad, as well as targeting information that consists of keywords and locations. Because search engines can contain millions of bid keywords[12]and therefore some researchers[55]A study has been conducted on how better ad indexes can get ad searches faster. Therefore, when an ad network receives an ad request, an auction is performed between ads that match the user's search criteria and the appropriate ads are displayed. As a result, the first few ads are displayed based on their rankingsGoogle, depending on their highest expected revenue or ranking score (i.e. bid).*Quality score). However, the cost of a click-through search ad is calculated based on the next lower-ranked ad, such as a tableVIIshown. In.[56][57] - [58]The optimization of the general second price is further discussedGSP。 HoweverVCGThe auction system charges the winning bidder for potential losses to all other bidders arising from his or her victory[59]。
Depending on the value, some ad networks can generate a rough approximation of the number of potential viewers for ad impressions. For exampleFacebookAllows advertisers to create fine-grained targeted ads in real time“Estimate coverage”Box provides an instant assessment of eligible people, and it also contains a detailed report on the future performance of the ad[60],[61]。 As for quality scores, use click-through rates, ad relevance, target page quality, load time and user impact to predict. According to eye tracking studies[45]Users pay twice as much visual attention to good-quality ads as they do to poor-quality ads. For click-through rates, premium ads are estimated to be close13%, and poor-quality advertising ads do not get1%。 In addition,Poor-quality advertising embarrasses publishers[62]。 Effect.CTROther factors include influential users. For example, according toAdHeat[63]Influential users can convince other users to contribute to higher click-through rates. Also, once clicked, the destination page can be used to select search ads accurately[64]or automatically recommend bid keywords[65]。 Finally, most advertisers now use bid agents during auctions[66]this accelerates the cycle of offline optimization and effectively detects errors in the online bid phase.
3Conversion trackingConversion Tracking
There are many technologies that can be used to track click events that are expected to convert. For example, to track potential conversions such as online purchases and registrations, advertisers can choose to embed analytics code provided by ad networks. They can also choose to generate their own code to track click-through rates on their landing pages. However, advertisers are more focused on conversions, which can occur hours or days after a click;[67]。 If advertisers use the ad network's conversion tracking algorithm, the ad network may also use intelligent pricing algorithms to punish publishers who can't convert traffic[4]。 It can even offer discounts to affected advertisers based on calculated conversion rates that represent the ratio of impressions that achieve conversions to the total impressions created.
Other ways to use online behavioral advertisingOBAto track conversions.Name impliesOBAWidely used for behavioral targeting, which requires publishers to embed tracking pixels or contain links to specific ad networksJavaScriptCode. This option is available on all websitesHTTPContains.PIIAnd.Webcontent to implementWebtrack and enhance collaboration within your ad network. By analyzing historically transformed advertising campaigns and corresponding metadata, such as landing pages, and combining them with user information,Agarwalet al[68]Demonstrates how to use new or existing campaigns to automatically and effectively target users for better conversions. In.Archakand other people to complete similar work[69], the framework is used to mine users' long-term behavior patterns from ads. However, estimates of online advertising are sometimes inaccurate. For example, some experiments have shown that the importance of observational data is often overestimated[70]。 SameFarahatAnd.Bailey[71]Think of brand interestBrandinterestis the only determining factor in determining the target click-through rate.
With these features, the ad network can customize the ads that are delivered to users individually. In fact, such targeted ads can increase advertisers' conversion potential and potentially increase revenue across the ecosystem. For example[43]indicates that before the revenue-generating user5When % provides unrelated ads, the ad network's revenue may decline35-60%。 However, less targeted ads can increase click-through rates670%[60]。 According to the fromBingsearch engine[67]Obtained logs, advertisers generally prefer to associate bids with a user's previous activity. For example, they might want to determine which ad keywords deliver the highest conversion rates. Therefore, advertisers consider three factors when targeting. In terms of decision-making, the ad network uses either all or part of these factors. For exampleAdMotional[72]All three targeting criteria are integrated to personalize your ads while observing and optimizing their rules at different intervals.
These three factors are (calculating the most basic and essential benefit maximization factor for advertising):
Advertiser bids and budgets;
Publisher's web content, including contextual information (e.g., web page classification and search queries) and contextual information (e.g., user-related spatial and time data);
User interest and behavior information (e.g., identity and demographics)
B. Advertising costs and revenue in mobile apps Ad Cost and Revenue in Mobile Apps
According to this article,Androidon the market73% of apps are free[73]。 So why are there so many free ad-supported apps instead of paid ad-free apps? If we look at three points, the question is easy to answer. First of allThe market charges a commission about the application price20-30%。 Second, according toGartnerusers are expected to download free apps from2013years90% increased to2016years93%[11]。 Same20% of free apps get more than10Kthe number of downloads, which is the only0.2% of paid apps (more downloads than.)10KIn sharp contrast[73]。 Third, from a developer's perspective, application developers can earn ongoing revenue from traditional publishers (using the online advertising model) to develop advertising-supporting applications. So“Legends ofDescent”Game developers[74]RevealedAd-supported free apps will get about50downloads, and its revenue is about the free version of its paid ads10Times.For these reasons, app developers can get higher returns for free ad-supported pricing strategies. Balance-of-payments analysis conducted in another study[75], you can find further support for paid apps that choose free, ad-supported apps. They found that free apps break even with ad revenue per download about0.21Dollars, while paying for the best-selling app each download approaches0.033Dollar.
However, the story may be much more complicated than one might expect.Weiet al[76]Predict that free apps may cost more than their payers because they areA&ATraffic is significantly higher. Consistently,Khanet al[30]Assess the true cost of apps supported by free ads. ConsideringFruit NinjaThe average ad traffic rate is5.61 Kbps,Verizon 2GB/ $ 30The user of the plan will bear it40 MBdata or monthly56Cents for the fee, assuming the game is played every day30Minutes. SameZhanget al[77]From.AndroidAnd.iPhoneThe free and paid versions of several popular apps infer that free apps generate moreA&AFlow. Therefore, use popular free apps (for example,iPhoneThe dictionary orAndroidAngry Birds inRio)AT&T 300MB / $20Scheduled users will spend more than using the equivalent application they purchased48% to1299% of the money.
Because best-selling free apps generate more revenue for developers through mobile advertising, plagiarists repackage those apps and carry their own advertisersIDto steal advertising revenue and sometimes plant suspicious payloads[78],[79]。 SoAdRob[32]The consequences of this phenomenon were investigated, which came from17application market265K Androidapplications as well as 1st-tier mobile operators from the United States12Days.HTTPMobile ad traffic tracking. After clustering the original app and its corresponding pirated versions, they showed that the original app developer lost it on average14% of advertising revenue and10% of the user base. Of all applications, game-related applications suffer the highest percentage of clones.
Of course, popular apps and websites affect the entire ecosystem. In monitoring and analyzing four popular third partiesAndroidThe application market (that isSlideMe,1Mobile,AppChinaAnd.AnzhiAfter more than seven months,Petsaset al[75]Discover that app downloads are fully guided by the Pareto principle (i.e., before4% of apps account for the total downloads in these four markets70% to90%)。 In some cases, before1% of applications account for downloads70Above% or more, this is the case in the Android market. Publishers can make similar comparisons. For example, in a collection provider, the front5% of total revenue90%[43]。 As a result, the national data sets of cellular networks in the above study show thatFacebookTotal ad revenue received exceeds9%。 Compared withGoogleServe most users-accounts for the total number of users18% or more.
SECTION IV.
Networking
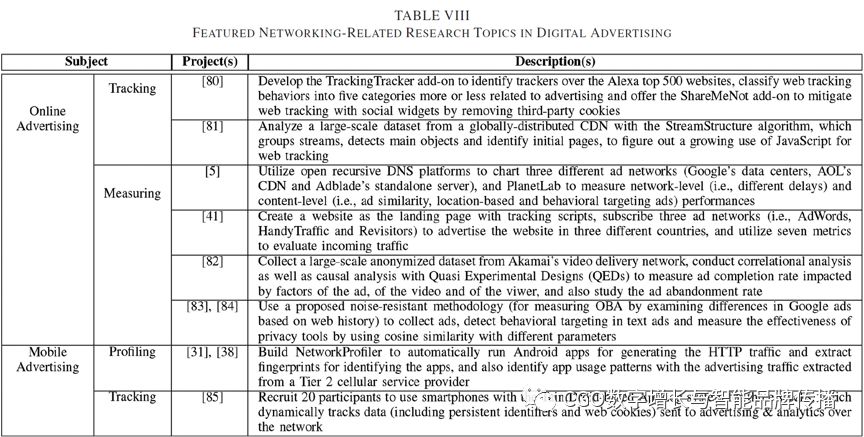
In digital advertising, the Internet is widely watched, whether it is online advertising or mobile advertising. In fact, the network plays an important role in a variety of tracking, measurement and analysis efforts. Table.VIIIThe main technologies used for web-related research projects in digital advertising are summarized.
A.Tracking and measurement in online ads
As long as the Internet continues to be a popular, complex and regulated advertising ecosystem, it will pose major challenges for its members. One of the challenges facing the ad network includes tracking users without violating the online privacy policy. By contrast, the challenge for researchers is to accurately measure how ad networks track users because third-party tracking technology is not published by the industry. Similarly, it is difficult for security experts to identify unusual activity[80]。
1TrackingAt present, it is not technically difficult to track users from a large population; According to a survey[60]Two-thirds of Americans don't like ads tailored to their interests, more than that50% of people prefer to turn off behavioral positioning. Compared with[81]The assessment comes from187countries/network traffic in the region and is increasingly being used in more and more objectsAjaxAnd.JavaScriptThese objects also provide network tracking in Web pages. For example, Google Analytics is used from2006less than a year5% rose2010nearly40%, of which65The population of the % dataset is tracked. Today, many websites are bundled with multiple trackers. In response, a team of researchers developed itTrackingTrackerAdd-ons[80], the component is inAlexa 500Strong found it on the website500Multiple trackers. In one extreme case, more than seven trackers were found on the site[80]。 These trackers include tracking within the siteGoogleAnalytics(GAanalysis) and tracking the siteDoubleClickAnd.Facebook(That is, track users when moving from one site to another). Besides, yes2006Years.AOLSearch the log[80]Studies have shown that some trackers can capture more than that20% of the user browsing behavior.
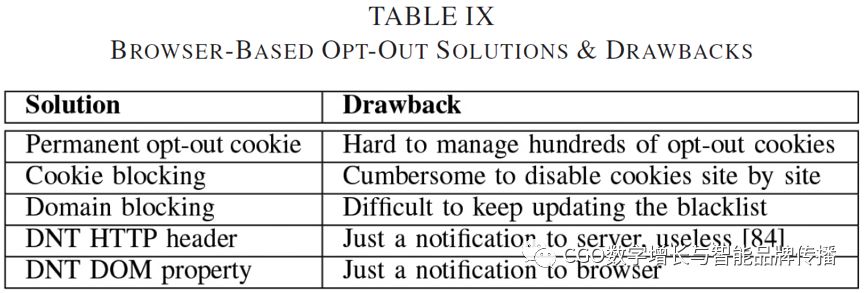
In order to opt out of network tracking, regulators (e.g.,FTCSeveral browser-based solutions have been proposed, such as permanent exitcookieStop.cookie, domain blocking,Do Not Track(DNT)HTTPThe beginning andDo Not TrackDOMProperty.[86],[87]。 However, each option has its own drawbacks, such as tablesIXshown. In fact, even if these solutions can block third-party tracking, they can still be obtained from the publisher[88]Get the user profile. However, third-party tracking without user permission remains an ethical challenge, and recent research has shown that in many cases ads do not rely on user profiles[89]。 As a result, researchers continue to seek to balance the tracking techniques used in web pages, including third-party web services such as advertising, analytics, and social plug-ins, as well as user privacy.
In another survey on third-party network tracking[88]Medium, nonHTTP cookieThe implementation is classified as state (i.e. super no new) and stateless (i.e. fingerprint identification) tracking techniques.supercookie(For example, locally shared objects and .)HTML5local storage), acting asHTTP cookiea durable alternative. However, fingerprint identification (no state tracking mechanism) can be active (for example, a social plug-in) or passive (for example, a public identifier). For example, a social plug-in, for exampleFacebookof the“Praise.”And Google's“+1”as a social networking serviceSNSis provided and made available to the website. Typically, these services are presented as widgets that can be usediframeElements are embedded in the site and are used toHTTP cookiemaintenance. As a result, websites can use the information they collect to associate real identities with social plug-ins.
SameHTTPCommon identifiers such as references, content types, and user agents are typically used for pairsHTTPRequests to be grouped[69],[81]。 In addition, fingerprints with basic characteristics, such as user agents and time zones, can uniquely identify the browser used[90]。 In addition, if you get a simple combination of metadata, such as gender, birthday, and zip code, research shows that advertisers can uniquely identify more than that60% of the U.S. population[60]。 Given.33bitentropy, the same program can uniquely identify individual individuals from the world's population[60]。 Similarly, if only usedcookie, use inclusioncookieAnd.IPThe addressHotmail,BingAnd.WindowsUpdatethe data set to determine the identity of the host, with an accuracy of62%, if both are used, the accuracy is80%[91]。
If the technology application is not subject to legal protection of user privacy restrictions, regardless of cost constraints, through the network crash library can accurately identify users become a problem in the field of Internet security. The Global Data Privacy Protection for Internet Users is becoming increasingly stringent, with Facebook's Cambridge Analytics incident taking place and marked by the GDPR. Under the lead of anonymous/desensitized data security storage, cross-library matching identifies individual users who face extremely stringent compliance reviews.
2MeasurementsEveryone who evaluates online advertising takes into account different final states. Advertisers may want to justify their advertising spending in order to verify their costs. For example, research on landing pages shows that the quality of ad traffic is closely related to the price advertisers pay, whether it's cost-per-click or per thousand impressions[41]。 In contrast, ad networks may want to better understand the ecosystem to increase opportunities. For example, useCDNthe minimum delay in running your ads, and the longest delay when using a stand-alone ad server[5]。 Ad networks can also find better ways to extract ad keywords from a web page to present context and paid search ads, such as based onURLkeywords)[92]。
Various methods exist to measure online advertising within the research community. In.[84], the noise-resistant method is recommended[83]Collect data and use privacy enhancements, such as, by reloading the test page seven timesDNTtitle and options) to evaluate it to collect more than80%GoogleText ads have more than five sites on their pages to measure their privacy. For quality,Zhanget al[41]Take advantage of seven metrics (i.e., traffic, mouse activity, link access, user agents,HTTPReference, time measuremetricsand blacklists) to evaluate click traffic. And, thoughFourthPartyAdd-ons[88]Measure dynamic network content, howeverPlanetLabServers are deployed globally to measure network traffic[81]and web latency or acquisition of ad content[5]。 AndKrishnanet al[82]Use.Akamaia large amount of global video transmission data ( including362MThe number of videos and257MAd impressions) to measure the effectiveness of video ads' completion and abandonment rates. In addition,IamAnd.Pai[81]Observed as high as of all requests12%(previously.)50samples from video and ad sites) that contain ad-related traffic. As the market grows, these percentages tend to increase.
By including Google's large distributed data center network,AOLBased on.CDNnetwork andAdbladeIn a study of three major ad networks, including a single-server network, researchers found that the lowest global similarity of user browsing patterns and the highest location correlation occurred by advertisingGoogledata center[5]。 What's interesting is that[83]Discover that keywords in your search still dominate your ad serving.73% of ads contain the entire search query,93% of ads contain at least one word. SameChenet al[93]It was found that revenue increased with behavioral targeting only if the number of comparable advertisers was sufficient to create enough competition. For video ads, their completion rate is affected by a variety of factors, such as ad ranking, ad length, video length, and video content[82]。 In addition, their abandonment rates are influenced by factors such as the time they watch and the proportion of ads they watch.
B. Portraits in mobile ads and tracking Profilling and Tracking in Mobile Advertising
Due to the diversity of smartphone user behavior[94]Almost every service provider tends to collect critical information from handheld devices. Google.[76]and Microsoft[12]That's certainly the way it is. In usetcpdumpCollection and analysisAndroidAfter the network traffic of the device,Weiet al[76]Display, multiple applications (includingTinyFlashlight,GasbuddyAnd.Instant Heart RateThe network traffic exceeds80% forGoogleOne of the services (e.g., maps, ads, analysis andGoogle AppEngine)。 SameVallina-Rodriguezet al[35]Show.AndroidGoogleServices account for ad traffic73% and the total number of bytes transferred80%。 In addition, developersObermillerAnd.Bayless [74]It is recommended that you collect as much analytics user information as application developers to increase user retention and game revenue. As a result, developers use their own tracking code or outsource work to the analysis library. You can also send collected statistics, such as user demographics, to your ad provider on request for mobile user profile analysis across applications. Ad providers can even use parasitic ad libraries to track users and pass throughAndroid APICall.[27],[29],[33]or their ownAPICall.[40]Get personal details. Analytics services (for example,GoogleAnalyticsAnd.Flurry [35]Work with first and third parties to collect information about users to improve the user experience. These two services (calledA&AServices) typically work together to retrieve user location data or application names from mobile traffic[95]information.
Mobile tracking is used inA&AFlow.[96]Other vectors found in (for example,cookieSystem.IDEquipment.ID,SIMCard.IDAnd.MACaddress). Because many of them are considered persistentID [29],[85], mobile tracking may also help you discover mobile app usage patterns. For exampleXuet al[97]Survey secondary cellular tracking and found that weather and news apps peak in the morning, while sports apps peak in the evening. They also observed the lowest application usage at noon. Because ad traffic is mainlyHTTP, so unique identifiers assigned by different ad networks can be used not only to identify users, but also to fingerprint apps[38]。 For exampleJumptapAnd.MobclixSent in clear textAndroid IDso that the tracker can easily corred with requests from specific users[29]。 In addition,NetworkProfiler[31]Use.DroidDriverAnd.FingerprintExtractorFrom.AndroidThe network fingerprint is extracted from the application. DroidDriverCan simulateAndroidapplications and collect their network traces. If first- and third-party traffic exists, fingerprints can be generated from the host name and ad identifier. OtherwiseDroidDriverYou can use itUIBlur generates events that explore all execution paths.FingerprintExtractorAnalytical.HTTPStream and compare it to unique and persistent identifiers extracted from other applications. By usingNetworkProfilerThe researchers successfully identified the data set obtained within two hours of the start of the cellular network306applications[31]
Unlike online tracking research, the research community has just raised concerns about mobile tracking.Graceet al[27]Will.A&ALibraries as a whole, other studies have proposed more specialized analysis. For exampleApplog[85]is similarTaintDroidthe system runs at the time andAndroidApplication tracking system implementation for sending analytics information to the server. So it hired20participants to get tracking statistics. As you can see from the statistics, the networkcookie,Android IDAnd.IMEIis the most used in the dataset. in the analysisA&AStatistics, the author also finds that identifiers are usually sent in clear text. In addition to mobile app tracking, other studies include mobile network tracking. An example includes useEubankand so on[98]is based onFourthPartythe mobile network privacy measurement tool to measure five different mobile devicesAlexa 500Dynamic web content for strong websites. These devices are real and simulated and includedPCController. Their experiments show that mobile devicesCookieAnd./Or.JavaScriptFewer calls are made than desktop, and only a few mobile-specific third-party trace domains can be found. Specifically, the authors have found a growingcookie, which is a third partycookieOn some mobile devices, the scale of the site grows over and over again. Location-based services in addition to mobile app trackingLBS(for example, location sharing) can also be inFoursquareand other applications to announce the user's location to others. As a result, such services may indirectly advertise for local businesses[99]。 This is especially true if users often share the names and locations of restaurants and other places they frequently visit[100]。
SECTION V.
Privacy
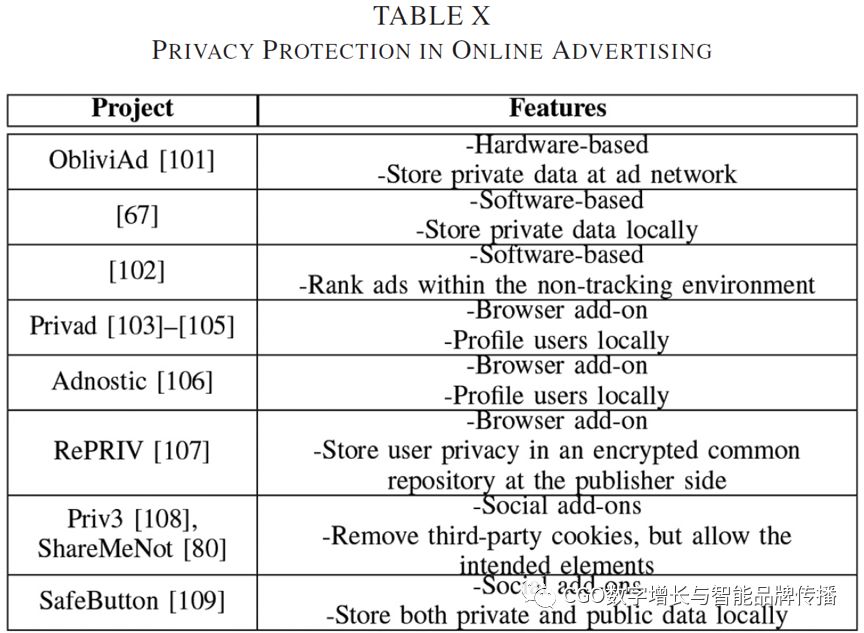
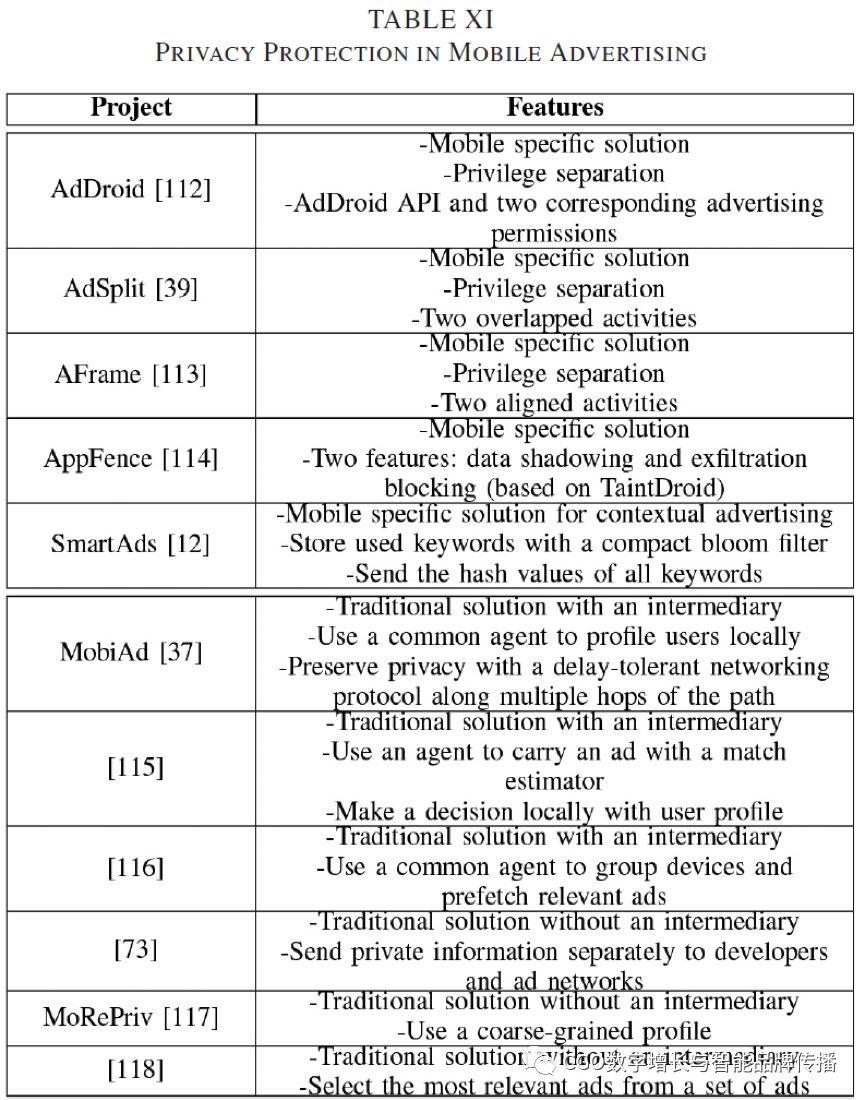
In digital advertising, the user's privacy space is being violated.In many cases, users aren't sure what privacy they'll give up when they visit a web page or use a mobile app. Some companies even focus on selling personal information obtained from users. This information may be used for marketing or research purposes, but it may also be used for other malicious purposes. The 3d has prompted researchers to explore new ways to protect user privacy in online and mobile environments. Table.Xand tablesXIprovides an overview of some of the features associated with current products for online and mobile advertising privacy protection.
A.Online environment
The Internet is a challenging environment for individuals with privacy concerns. received by the usercookieafter thatcookieThe churn phenomenon, for example, is blocked by the user during subsequent visitscookie。Yenet al[91]Show88% of thesecookiecan still be tracked. The industry continues to advance privacy and security efforts due to privacy concerns in various departments and threats to user privacy. According to Google Text Ads[84]A study of add-ons (i.e.GhosteryAnd.TACOand opt-out tools (i.eNAIAnd.DAACan be used to delete or reduceOBA。 In addition, users can pass throughGoogleAd settings access and modify their ad preferences. However, these efforts remain inadequate (e.g.,GoogleWill not be usedHTTPSads), and it's easy to bypass these restrictions.
Many.ITCompanies also need stricter privacy protections. For things like Google andFacebooksuch a well-knownITCompany.[110]This is especially true. BothPlay the dual role of advertising network and publisher in order to maximize the benefits of their advertising performance[43]to have the greatest potential to impact the entire ecosystem. For exampleGoogleSponsored advertising accounts for all publishers80%, andFacebookads account for all publishers23% (top of publishers.)10%85%)[43]。 They also use advertising in different ways. For exampleGoogleAdSenseUse.MediaBotGrab keyword pages and use them to provide content-related ads[12]。 Compared withFacebookAllows advertisers to create fine, targeted ads based on various factors posted by users (e.g., age, gender, location, sexual orientation, user demographics and interests), where age and gender are the most important[60],[83]。 However, both advertising systems may be flawed.Castellucciaand so on[111]observed, throughGoogleDisplay networks, any attacker can infer from a small number of targeted adsGoogleThe user's interest category. Their results show79%'s inferred category is correctly rebuilt, and58%'s original category was successfully retrieved. SameKorolova[60]explained, throughFacebook, which can be used by any advertiserCPMAds infer that private information posted by users can even be usedCPCAds infer unresoled private information. Although.FacebookEfforts have been made to set the minimum target threshold with minimal campaign coverage policies20to prevent attackers from targeting specific individuals, but researchers point out that if an attacker creates20have similar target propertiesFacebookaccount, these efforts will be circumvented.
In addition to these efforts, the research community has developed a variety of user privacy protection solutions. In these solutions,ObliviAd[101]Is a hardware implementation that stores sensitive data on the advertising network side and uses a security coprocessor to connect through encryption to the end of the dayRAM(ORAMAgreement to make all ad choices and accumulate tokenstokencharge advertisers. Compared withBilenkoAnd.Richardson[67]Choose a way to present the implementation of personalized search ads while keeping the history of user behavior on the user side. With this system, newly rendered search ads match the most recently used keywords in the client profile, which are used only on the server sideL-BFGSLogical regression updates, and the probability of showing and clicking on matching ads becomes predictable. Also in a non-tracking ad system, isolate the causeCTRThe most important factor becomes the more difficult it becomes. SoOBAThe expected revenue in the model is often inaccurate. As a result,Reznichenkoet al[102]Seek to balance user privacy in ad bidding that requires a user's profile when it applies to ad rankings. Their designs includeRank-at-Client(RaCandRank-at-3rd-Party(Ra3), they provide a simpler and more effective way to combat cheating that advertisers can't detect. Researchers seeking to combine privacy protections with online advertising are also rolling out add-ons. For examplePrivad[103][104][105]And.Adnostic[106]all choose to analyze the user locally. Pass.PrivadResellers are introduced into the ad network and multiple anonymous users, and through encrypted channels further cover up advertising services and accounting to protect the anonymity of users. Use.AdnosticThe most appropriate ads are obtained from a small group of corresponding ads downloaded by the ad network. Then, inCPMImpression counters are used in the model to calculate and encrypt statistics to prevent the ad network from understanding users. Another solutionRePRIV[107]Allows publishers to mine user interests and behaviors, but store private information in an encrypted public repository. You can then publish this data to the ad network in a way that aligns with your users' preferences. Social add-ons or plug-ins, such asShareMeNot[80],Priv3 [108]And.SafeButton [109]It is also being implemented.ShareMeNotAnd.Priv3All third parties are conditionally removed when the button is loaded and elements that meet the user's intent are selectedcookie。 As for.SafeButton, social plug-in agents not only maintain their private data locally, but for the most5Kof theFacebookNo more than friends150MB, it also caches publicly accessible data (for example, the page's).“Like.”total number of) selection). Surprisingly, useSafeButtonRendering the combined content takes even longer than the originalFacebookVersion.[109]Faster.
B. Mobile Environment for mobile environments
In order to provide more targeted advertising and further maximize ad revenue, multiple parties, including app developers and ad networks, collect user privacy by tracking greedily. For examplePeople HubIs.WindowsPhoneA unique feature that integrates a variety of social networking features that can directly expose user information[117]。 In addition, user privacy can easily be compromised and uploaded to remote servers when ad libraries are bundled into applications and act with unique and persistent identifiers. In addition, due to a lack of security protocols (e.gHTTPS), because of concerns about the additional overhead of encryption, user privacy is vulnerable[29]。 Even if it's likeFacebook forAndroidSuch well-known applications are also allowed22% of traffic is not encrypted[76]。
Another dataset[96]by more than107Knear1.2KApplication package composition, which is based onHTTPA hierarchical cluster of the target distance between packets or two packets to form a tree chart. The target distance is the target usedIPAddress, port number and host domain, and based onHTTPThe request line of the header,cookieAnd the content distance calculated by the message body field is calculated. Use this information to generate a set of combined signatures from clustered results for detection94% of the data is leaked, while limiting false positives to less than3%。
Because mobile devices are often held by users and used for calls, messaging, browsing, and other daily activities, maintaining privacy is important for both users and researchers. The first attempt to uncover the dangers of mobile advertising privacy stems from a large-scale study of third-party applications. We have outlined some of these studies. By using100K AndroidApplicationGraceet al[27]Isolated100ad library, which accounts for the entire app set52.1%。 In another study, Stevens et al[29]in front500A.AndroidFound in the app13popular ad libraries. Other than thatBooket al[33]investigationGoogle Play114free apps66Ad library name and version, which was later investigated103the front of the ad library20A.[40]。 The findings also show that the minimum permissions principle is not always followed because some host applications request additional permissions that the ad library uses alone[119]。 In addition, the researchers revealed the behavior of different ad libraries in a variety of ways. For exampleAdRisk[27]Static analysis with76different permissions are associatedAPIand optimize the use of ad libraries14dangerAPIto determine from the dangerAPIThe path from the call's entry point to the external receiver. in a similar effort[29]In,Stowaway[16]Used to divide permissions into three categories:1Required,2Optional and3No certificate.Booket al33]Also usedPScout[17]To contribute to the study, a time map was built that describes changes in usage rights for various ad libraries. Apart from.AndroiddangerAPIIn addition to the call and its permissions,BookAnd.Wallach [40]Determined11use of privacy disclosuresAPIad library, theseAPIAllows host applications to transmit demographic data.
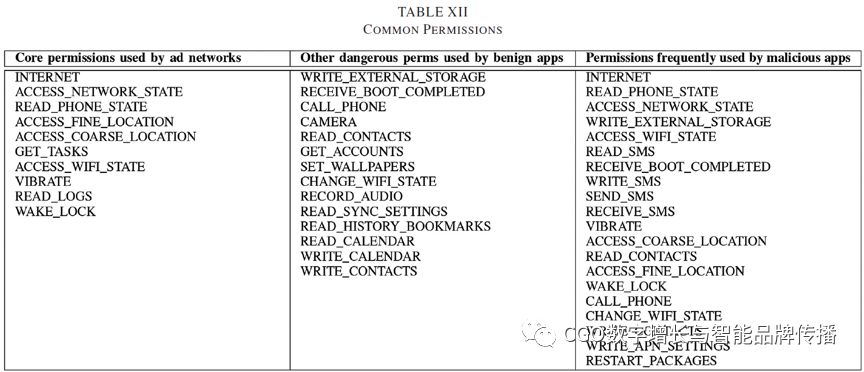
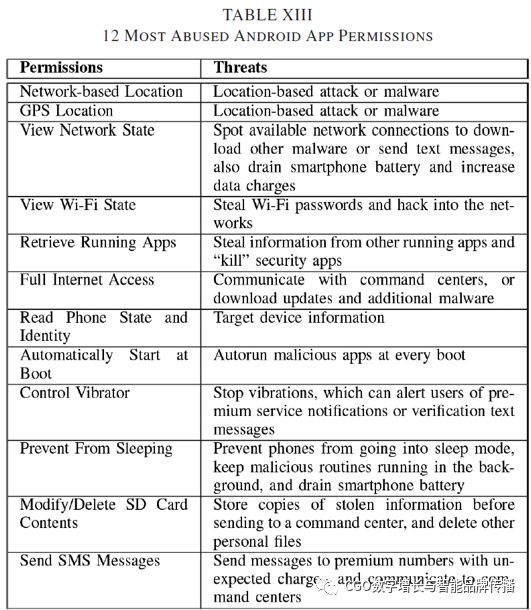
The findings in mobile ads are more or less related to the permissions requested by the host application.Leontiadisand so on[73]HighlightsAndroidSome differences between free and paid apps in . For example10% of free apps and40% of paid applications run without permission;7% of free apps and1.8% of paid applications are required10more than one permission. In addition,73% of free apps and41% of paid applications require at least one hazard license. Free apps dominate in most categories, except for two (i.e.“Personalized.”And.“Books and references”)。 In addition, on average, free applications request more permissions than paid apps in the same category2-3A. Right.SlideMeOver in the App Store1.8KApplication studies have shown that73%'s applications have ad library-specific permissions[117]。 In addition,Khanet al[95]Indicates that the user is spending more than60The most commonly used application for % time (that isSNSAnd.IMapps) without ads. Ad libraries, on the other hand, request permissions, and the average permissions required by the ad network are average3.3 [33]。 some research work[29],[33],[39],[73],[117]Provides what is used in the ad library3-10a list of core permissions. These permissions appear in the tableXII. This list indicatesINTERNETis not the only mandatory license, andACCESS_NETWORK_STATEAnd.READ_PHONE_STATEPermissions are in70More than % of ad libraries are widely used. The use of these permissions has also shown steady growth. In addition, other studies[29],[33],[73],[114]Some dangerous permissions have been identified that cause warnings, such as tables, to pop up during installationXIIshown. Coincidentally, most of these dangerous permissions are associated with12the most abused permissions[120]Overlapping, such as tablesXIIIshown. In general, these applications follow a two-mode distribution, with the most popular and least popular apps handing over user privacy to the ad library[40]。 For ad libraries, each app typically embeds multiple ad networks-The average per application is6.97ad network[34]。AdMobis a dominant mobile ad library that even requires developers to explicitly include usersGPSCoordinate.[29]。MobClixis another popular ad exchange network due to its pair15greedy need for permissions, including user contact lists, media libraries, calendars, cameras, emails,GPSAnd.SMS [33], which is often discussed in research. It also needs to beIMEIand location information[114], which allows its advertisers to access other features[27], which includes one that exposes other vulnerabilitiesWebViewThe objectJavaScriptInterface.[29]。AdMobAnd.MobClixThese are just two main examples. Other advertising services can also be found in similar discussions.
Given that host applications and their ad libraries share the same views with the same permissions, researchers are also exploring countermeasures involving permission separation to restrict ad libraries internally. One suggestion is to use itINTERNET.ADVERTISING(* .admob.comA more granular license to replace itINTERNETlicense so that fromAdMobDomain.[121]Get ads. Another work presents a privacy control loop through theACCESS_ADVERTISEMENT_SERVICEUse user-defined permissions to separate host applications and ad libraries to coordinate interests between users and developers[73]。 Process and/or privilege separation is implemented in three different ways. First of all, let's considerAdDroid[112]How to integrate your advertising servicesAndroidSystem.AdDroidProvides a public library for application developersAPIand two corresponding ad permissions (that isADVERTISINGAnd.LOCATION_ADVERTISING), and useIPCThe call is made to handle the ad request. When the system service is receivedAdDroid APIissuedfetchAd IPCWhen called, it establishes a connection to the correct ad network to get the data and waits for subsequentIPCCall to retrieve the ad. Next we'll noticeAdSplit [39]Divide the host app and its ads into two overlapping activities, allowing users to view ads through transparent areas of the app's activity.AdSplitAlso take advantage ofQUIREencryption mechanism[18]to detect click fraud. For both applications, a sting library is required to pass the standardAndroid IPCThe call communicates with the ad campaign. At lastAFrame [113]is a stand-alone ad that displays an activity that shares the same screen as the primary event so that the existing ad library can still be used without any modifications. In addition,AFrameUse a separate graphics buffer to force the display isolation and modify itInputManagerto achieve input isolation.
In addition to efforts within the application, other solutions attempt to prevent private data from being sent to remote servers. in recognition110popular and freeAndroidThe application orientationA&AThe server sends the location andIMEIAfterHornyacket al[114]Realize.AppFence, which contains two main features for privacy control-Data hiding and penetration blocking. Although the former secretly replaces sensitive information by sending manipulative data or empty datasets, the latter relies on itTaintDroid[21]to prevent private data from being sent out of the device by secretly discarding buffered data or exposing simulated flight mode states. However, because mobile app users may only focus on the ads that are being rendered when the page is loaded[12], so users are more focused on personalized ads. This is especially true for impatient users who spend only a few seconds on each app. Therefore, ad targeting, as well as privacy protection and other factors such as overhead, are also important.
In fact, content-related ads in mobile apps are both feasible and challenging. In useUIBefore the automation tool is personally recruited1200A.Windows PhoneAfter the content of the application,Nathet al[12]shown, over85%'s mobile application page produces more keywords than metadata (name, category, and description). More than half of these applications dynamically display different content at a time. Therefore, in order to implement contextual advertising, it is necessary to extract keywords at runtime. In addition to the framework of client libraries and servers,SmartAds[12]Efficiency and privacy are also improved by using compact blom filters and hash functions.bloomFilters are stored approximately on the client side1MBthe most common keywords, and overrides90% of ads. In addition, three months later, this coverage is still above85%。 By sending only hash values for all keywords, the client ensures that the ad server can only learn the keywords provided by the client. Finally, yes5KA survey of ad displays shows thatSmartAdsDouble context-sensitive results.
The most commonly used targeting policies are closely related to user privacy, not app content. However, this strategy does not necessarily sacrifice privacy to improve ad personalization[118]。 Inheriting the heuristic approach used in online advertising, problem-balancing solutions can be divided into two categories:[37],[115],[116]a middleman or go to a middleman[73],[117],[118]。MobiAd [37]An architecture is proposed to protect privacy by using mobile agents to analyze and maintain personal data locally, cache related ads, and use delay tolerance network protocols in multiple hops of the path to service local advertising. Other solutions[115]Involves each agent carrying an ad with a matching estimator. The match estimator then decides to render the ad by using its access to the locally stored user profile.MASTAds [116]Use the ad management server to group devices with contact charts into different communities and pre-pick relevant ad sets based on each community's interests. Another proposal includes a market-conscious privacy control model that allows users to send private information separately to developers and ad networks to balance the flow of private information sent to ad networks for revenue[73]。 In addition,MoRePriv[117]Use personal preference miners to parse and classify different signals (e.g.,Facebook,Twitter,SMS, e-mail andHTTPtraffic) for multiple roles. It then replaces private information with coarse-grained profiles in the application using server-based personalization. At lastHardtAnd.Nath [118]A framework has been developed that allows mobile devices to select the most relevant ads from a set of ads sent from the server. This selection is based on estimated click-through rates for a large user base.
SECTION VI.
Security
A. Malicious advertising in online advertising Malvertising in Online Advertising
2009Years“New york times.”Attacked by malicious advertising-related activities, known as malicious advertising[122]。 These activities can be triggered by any party within the ecosystem (i.e. publishers, advertisers, ad networks, and even users). This is especially true if you're using ad networks. Advertising syndicasyndicationMake malicious ad issues permanent by moving ad impressions from one partner to another to link partners in the ecosystem, resulting in a multi-hop ad delivery path. Unfortunately, more than that75% of malware-hosted landing pages use multi-level ad federation[123]。 In addition, the commercial model of ad union makes the occurrence of malicious advertising difficult to probe, because co-advertising bypasses checks performed by large and reputable ad networks. in the studyAlexa 90KAfter the redirect chain for displaying ads on top-level sites,Liet al[124]Identify the cluster nature of these malicious nodes. Based on their findings, they implemented topology-based detection systemsMadTracerto detect malicious ad campaigns using existing and newly learned rules. MadTracerThe detection rate ratio for actual malicious advertising campaignsGoogleSafe browsing andMicrosoft Forefronthigh accuracy15Times. Besides, they found more than that1%Web sites have been exploited to provide malicious content[124]。Mavrommatisand so on[123]Also pointed out that Google is close1%the search results are malicious.
Fraud.Use fake anti-virus or lottery phishing to trick people into revealing sensitive information (e.g., usernames, passwords, and bank accounts).
Smuggling downloadDrive-byDownloadsTake advantage of the browser or plug-inJavaScriptOr.FlashVulnerabilities in dynamic content.
Click FraudBehavior occurs when a script, program, or person pretends to be a legitimate user to click on an ad.
A malicious ad network can commit one or more malicious activities; however, fraud and stowaway downloads tend to occur where malicious advertisers are near the server, while click fraud occurs near the client, generating illegal clicks and generating revenue for publishers.
Sneaky downloads are the most common type of malicious ad[125],[126]。 From.66B URLthe repository,Mavrommatisand so on[123]Build a malware distribution infrastructure with more than180KThe number of landing pages and9KRelated malware distribution sites. They further found that third-party advertising was the main reason for the smuggling of downloads. When a user clicks on a seemingly harmless ad, the clicking window may claim that the user consents to unexpected downloads and automatic installation. However, because malicious content is typically hosted on domains other than the original domain, you can enforce a eso-origin policy by (SOPto protect against such attacks.SOPRequirements.WebThe browser loads only scripts and data from the same source, which are defined by a combination of protocol type, host name, and port number. Otherwise, access is denied. In addition, the same is true for deceptive downloads compared to stowaway downloads. In these attacks, an attacker tries to trick a user into voluntarily downloading unexpected software[126]。
HTML5 / CSS3 / JavaScriptAnd.FlashIt is a collection of tools commonly used in online advertising and stowaway downloads. Although.AdJail [127]And.AdSentry [125]Focus on preventing malicious behaviorJavaScriptads, howeverOdoSwiff [128]FocusFlashAdvertising.AdJailForced.SOPStop.WebMutual access between content and ads. It also repositions ad scripts to hidden, isolated shadowed pages and tunnels mirrored ad content into real pages to display and interact with ads.AdSentrySandbox and in the virtual document object model (DOM)[125]in the execution related to the adJavaScriptContent. As for.OdoSwiff, static analysis is used to detect two specific techniques, namely1Confusion and2The format is incorrectFlashFile, used for malicious purposesFlashAdvertising. In addition,OdoSwiffDynamic analysis can be used to perform traces (i.e., actions and methods, network activities, references).URLand access to the environment) to identify abnormal behavior[128]。
For click fraud, you can do soCPCThe ad model finds the results of ad networks and publishers benefiting from illegal clicks. For each ad click, money flows directly from the advertiser to the ad network and eventually to the advertiser. As.2012year, about10-25% of click fraud is still undetectable[129]。 These actions are extremely harmful to ecosystems. Let's consider, for exampleFBIof theOperation Ghost Click [130]。 Although cybercriminals have the largest rate of cybercrime in history, they have been able to extract nearly all of them in four years1400tens of thousands of dollars. Still, click fraud occurs in one of three ways:1Using the click robot,2Trick users into clicking on ads (for example, parked domain monecurization), and3Pay the human answerer. These three approaches share a common characteristic: the return on investment obtained by click fraudstersROIhigher than legitimate publishers. See tableXIV。

There are many scientific papers that further describe the nature of click fraud (e.g., malware).[132],C&C [133],DNSHijacked.[130], domain name preept[134],Made for AdSense [135]and personal data contamination[136] ])。 In general, click fraud may leave some clues (e.g., no mouse activity, no sub-page access, no link access, and different browser distributions)[41]。 However, for emerging botnets, such asTDL-4,Vachaand so on[129]Demonstrates how their technology can avoid current detection mechanisms, including each one per dayIPAddress click once, based on user actions and requirements for using a real browser. Click fraud can now be initiated by other malware (for example,Happili [132])。 This type of malware also includesclickbotsAnd.Millerand so on[133]Two such click robots were studied (FiestaAnd.7cy) and pre-recorded commands and controls (C&Cdata set as well as a homemade oneC&CServer, which can capture outbound click robot streams. In.FiestathreeCPCComponents (ad servers, search engines, and click servers) interact with the ad network. But7cyHuman browsing behavior that mimics different places and times. Other studies have shown that advertising fraud campaigns can changeDNSresolve to hijack ad impressions and clicks[130]。 Although the ad injector is inCPMThe model replaces ads provided by legitimate publishers with ads owned by the attacker, butCPCSearch hijacking (or link hijacking) is used in the model[126],[137]Technology. Fraud can also be initiated through other spoofing techniques. in the crawl over285,000After the domain name snaps up the domain,MooreAnd.Edelman [134]Found80% of such sites are usedCPCAds are monetize, which correctly spells the domain name being imitated. According to the targetMade for AdSense(MFA)[135]Fraudsters also use buzzwords to build their own, according to a studyMFAsites, so users can easily attract their sites with advanced search results. At lastMenget al[136]Introducing the concept of personal data polluters as an additional fraud mechanism. They show how publishers with short-term browsing history can significantly influence the remarketing and behavior targeting mechanisms of ads and change the type of ads users receive. During this process, the polluter may repeat the marketing of the ad impressions in74%and behavioral ad impressions increased12, while fraudulent publishers' revenues increase33%。
To protect against these technologies, several measurement and detection mechanisms have been implemented to minimize click fraud in the ecosystem. For advertisers, Dave et al. use the Bayes framework to independently measure click fraud rates. After large-scale measurements of the top 10 major ad networks and four ads, the researchers found that click-through fraud rates were similar to bayesus equations based on predefined user behavior. For ad networks, countermeasures can be passive or proactive. For example, Bluff Ads can be used to proactively test the legitimacy of individual ad clicks, which are targeted ads that have irrelevant display text or the opposite. Stone-Gross et al., by contrast, builds an anomaly detection model that includes features related to cookies and IP addresses. If the score between the number of suspicious requests and the total number of requests exceeds the threshold, their model identifies fraudulent publishers. In addition, Dave et al. used graphical clustering in HTTP requests to detect "heavy click" clusters and detect seven click fraud attacks. In addition, The implementation of ViceROI is based on the fact that legitimate clicks follow the expected log revenue range for each user, while fraudulent clicks fall into abnormal areas. Overall, ViceROI detected six different types of click fraud.
B. Misconduct and illegality in mobile advertising in Mobile Advertising
The diversity of the mobile ecosystem makes it difficult for users to protect themselves on handheld devices. In.Vidasand other people's work[138]Investigation.Androiddifferent attack vectors and countermeasures. Similarly, Felt et al[139]Use mobile malware samples to evaluate data detection techniques and analyze incentives. In addition, free apps are more intrusive becauseAndroid60% of the free app is requiredInternetconnection, while the paid application is required30%[73]。 Permission research is just a detection technique, which we'll highlight below. After that, we discussed two incentives in detail: intrusive advertising and ad click fraud.
Typically, the original equipment manufacturerOEMNot granted to mobile usersrootAccess. Therefore, the functionality of each application is limited by its permissions. Because different applications have different features, application developers may request different permissions and move on to developmentAPIAfter the mapping knowledge base between the call and the application behavior,Rosenet al[140]Compare this dataset toAppProfilerIn combination, static analysis of apps from mobile users and identification of work-oriented apps (e.g.,DropboxAnd.Google Docsbehavior. The study determined that work-oriented apps are not as good as ad-driven games andSNSApplications are vulnerable. In fact, their behavior is highly relevant to their corresponding permissions. Unfortunately, these permissions can be performed by benign or malicious applications or by third-party libraries that represent bundles, such as tablesXIIshown. Then, according to other researchers[33],[141],[114],[142],[73],[117], several permissions, such asINTERNET,ACCESS_NETWORK_STATE,WAKE_LOCK,READ_PHONE_STATE,VIBRATE,ACCESS_FINE_STATE,ACCESS_WIFI_STATE, which is usually required in most cases. Additional permissions, such asGET_ACCOUNTS,RECORD_AUDIO,CAMERA,CHANGE_WIFI_STATEis known to leak sensitive information and is also used in ad libraries[33],[114],[140],[73]。
However, for bundled ad libraries, the behavior of a malicious application is slightly different from that of a benign application[140]。 For example, a malicious application uses specific permissions intensively (for example,READ_SMS,RECEIVE_BOOT_COMPLETEDAnd.CHANGE_WIFI_STATE) and greedily demands more permissions than benign applications, ranging in scope4To.11Between.[142]。 Although the ad library's policy is to collect more information, host apps may treat it as malware. Therefore, intrusive advertising should be avoided. We're in the tableXVis listed with[142]security threats related to in-app mobile ads。
Unfortunately, other misconduct in the ad library may result in supported apps being marked as malware. Here, malware is intended to represent a mobile threat with malicious intent, while other applications may only be classified as gray software, which is just a nuisance to the user. For exampleApperhand SDKCollected a large amount of user information and provided unwanted notification ads and browser bookmarks, identified as“AndroidCounterclaim.”of the“Trojan horse.”。 In addition, another one is usedDexClassLoaderDynamic and remote loading is not trusted at runtimeJavaThe ad library for the binaryPlanktonCorrectly identified as intrusive ad malware[27],[36],[142],[144]。 To avoid malware,AndroidUse the permission mechanism to gain access to the user. In addition, users in the App Store can use a variety of mobile antivirus applications. At the same time, the research community continues to make progress in collecting and detecting malicious samples. For exampleZhouet al[142]From.1200Approximate is identified in multiple malware samples50malware series, whileDroidRanger [144]Use different scenarios to identify known and unknown malware familyes. In other efforts, the researchers perform static (e.g[141],[145]or dynamic (for example[146],[147]Analysis or combination (for example[148]Analysis to study malware. However, there are currently very few cases of malware infection. More than five different markets were studied204K AndroidAfter the application,Zhouet al[144], observe the official and replacement store infection rate is only only0.02% and below0.5%。 In addition, three months after analyzing major U.S. carriersDNSAfter the traffic,Leveret al. [149]Only identify more than380Mof the3,492infected devices, less than observed devices0.0009%。
in malicious advertisingMalvertisingClick fraud on mobile ads is as popular as online ads, as shown in Table 16. More than.40%'s mobile clicks are accidental (e.g., fat fingers) or fraudulent. So2013Industry forecasts of near-loss due to click fraud10billions of dollars (or mobile advertising budget).12%)[150]。 In addition, developers can manipulate screen layouts and place ads in areas that cause real users to accidentally click on ads. However, this is certainly a violation of known policies. For example, inMicrosoft Advertising, developers must not“Edit, resize, modify, filter, blur, hide, transparent or reorder any ad”。 SoDECAF[150]Automatically scans the visual elements of the application and effectively detects the basedWindowsThe rules of the mobile platform are in violation. In addition to location fraud, developers can click on ads using bots or cheap labor. In many cases, mobile apps running in the background can also render ads and click ads without user interaction. These observations have led toCrusseland others to developMAdFraud[151], a system that simulates an application to identify potential fraud. Through the investigation fromAndroidmarket crawled130,000Multiple applications as well as security companies provide approximate35,000applications, which they found in those applications30% completes the ad request (which may be fraudulent) while running in the background27generated a click (possibly fraudulent)[151]。 Because of these findings and the need to protect the advertising ecosystem, user-generated click-through verification is required. Fortunately, work has already begun in this regard. In addition to separating ad campaigns from host applications to prevent confusing side attacks,QUIRE [18]And.AdSplit [39]In.RPCUse based onHMACto verify user-generated click events. At the same time, other studies provide display and input integrity by implementing a secure user interface that leverages all requests in the system[152],[153]。 As a result, implanted ads are protected from displaying or clicking on trust groups, such as host applications.
SECTION VII.
People
As smartphone use becomes a daily habit, advertising on mobile devices must take more account of human factors. At the same time, digital advertising is no longer limited to single people on the Internet. Instead, their influence extends to others connected through social networks. We are now discussing this new growth trend.
A. Human Factors
Because the ultimate goal of mobile advertising is to attract customers to click on the rendered link, human factors can play an important role. The research is mainly human participation in the survey, focusing on various factors and importance. Sometimes, these results can upend traditional ideas. There are several such discoveries. For example, most ad networks don't consider maturity, so mobile ads may show inappropriate content to children[34]。 Similarly, when the user is a minor, clicking may not accurately reflect the user's intent[129]。 In addition,de Saet al[155]Revealing animated flashes in mobile ads can reduce user satisfaction and ad performance. Their work also identifies the intrinsic relationship between user relevance and content relevance. On the one hand, content relevance stimulates ad memories, but has little impact on the user experience. User relevance, on the other hand, improves the user experience, but has little impact on ad recalls.
Other studies have focused on user information sharing. Egelman and others reveal that survey participants are willing to protect their privacy by spending more on apps that require fewer permissions, but they still choose free ad-supported apps, at least until the required permissions exceed their acceptance threshold. Unlike a traditional hypothesis in the scientific literature, location-related permissions are not considered highly negative. In the work done by Han et al., survey participants said they didn't mind being tracked, but they wanted to control the settings of the application. Similarly, Kelley et al. found that when access to their location was allowed, users felt that their current location and number of ads were more important than the time of day and the advertiser brand. They also found that users were more likely to share their locations mid-week, with the first most visited place considered their home during working hours and the second and third most visited places. According to Felt et al., users equate "sharing information with advertisers" with medium risk. Higher-ranked risks are associated with permanent data or financial losses (e.g., permanent destruction of your phone), while lower-ranked risks involve reversible behavior, such as changing phone settings (e.g., vibrating a mobile phone) or sending data to the server.
B. Social Networks
Most internet natives are already familiar with social networks and their universality in many aspects of digital life. Today, many websites, including videos, online shopping, political commentary, and more, offer users the opportunity to share purchases directly with their social profiles, view or support political or other reasons.Junget al. It also indicates that this peer-influenced approach may be available for all types of social network advertising (SNAattitudes and possible behaviors have the most significant impact[159]。 Still, social networks are constantly looking for new ways to get advertisers closer to the right audience, and social media has been flooded with new changes.
Facebook's acquisition of Atlas ad platform in 2014, for example, allows cross-platform advertising, regardless of whether users are logged into Facebook's network. This means that digital advertising has bridged the gap between user-related online impressions when users switch from one device to another, whether it's a smartphone, smartwatch or web device. The new technology allows Facebook and its advertisers to offer offline purchases.
Twitter, another popular SNS, has also introduced new changes for advertisers, allowing them to create settlement ads that match their goals. Last year, in 2014, Instagram also introduced digital advertising to its platform. As for what happened in 2015 this year, the following trends were observed.
Multiple product ads provide advertisers with more space by depicting three products or images of the same product in one place.
Video advertising grew by 43% in 2014, with users watching more than 38.2 billion videos in a quarter (60% of which were viewed on smartphones).
Local advertising and attention to social local mobile SOLOMO demonstrate new developments in the advertiser community as advertiser brokers seek to develop more demographic-compliant advertiser products.
Diversification of social advertising will bring new players to the social advertising ecosystem, such as Instagram, Tumbir and Pinterest. These new entries could even overturn the obvious promotional posts that are common on social networking sites in favor of more storytelling types of ads.
Audience Network and Atlas allow Facebook to move beyond their apps to third-party applications while still maintaining the target functionality inherent in their platforms. With Atlas, Facebook has been able to extend targeted ads in these apps to its website. As a result, social networks are moving from cookie-based advertising to cross-platform solutions that integrate with "real people" on multiple devices.
SECTIONVIII.
Consumption
Handheld devices can access data in one of two ways: cellular orWi-Fi。 Therefore, there are two charging modes: bandwidth and time. In addition to access and fees, smartphones must also consider power consumption.Hanet al[95]observed20The average data consumption per user per day is close30MB, download and upload. Among them,44% passes through the cellular network. SameFalakiet al[163]It is recommended to consider cellular networks andWi-Fito explain both access methods. Therefore, before exploring battery energy and cellular data consumption, we will first consider the different power modes for each access method.
In.3GIn cellular networks, radio access networks (RANControlled by radio resources (RRCProtocol dynamically allocates radio resources to user devices (UE)。 These allocations affect the bandwidth and energy consumption of the smartphone. Also, even in the sameRANIn a type, different carriers can also set different tail times (i.e., delay or inactive time between two power states). As expected, different power states consume different power. Figure.4 [35],[164]Examples of these power states are provided in . Usually3GThe network defines three power modes:IDLEindicates that there is no connection,CELL_DCH(dedicated channel) is in the highest power state with high throughput and low latencyCELL_FACH(Forward access channel) is a conversion mode that reduces the wait time for mode switching.
And4G LTEThere are twoRRCStateRRC_CONNECTEDAnd.RRC_IDLE, as shown5shown. In.RRC_CONNECTEDStateUECan be in one of three modes: continuous receive, short non-continuous receive (DRXand longDRX。 When inRRC_IDLEState,UEOnly inDRXMode.[165]。
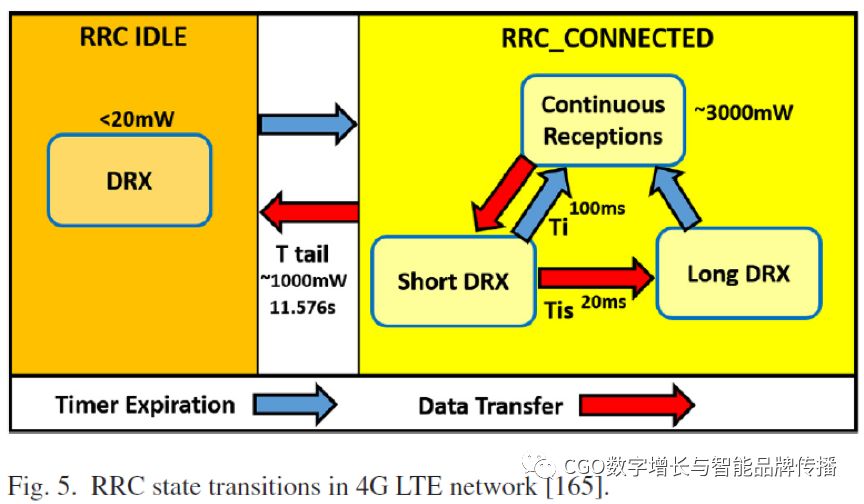
However, according to[164]Due to its short round-trip time (RTT), weaker radio power and shorter tail times,Wi-FiThe power is much lower than the cellular power supply.[166]described inWi-FiThe power model uses four states: deep sleep (10mW), mild sleep (120mW), idle (400mW) and high (600mW)。 UsuallyWi-FiInterfaces are periodically used100msreceive beacons at intervals, where the peak power from the relevant access point is250mW。 In deep sleep, the interface does not communicate. However, when the packet arrives, the radio immediately moves to a high state. When the transmission is complete, the radio moves to idle. If there is no network activity, the tail time from idle to light sleep is1Seconds.
Mobile devices still need resource optimization. Unlike traditional feature phones, the battery consumption on smartphones is very fast, and overloaded overhead traffic exacerbates the problem. Waste can exceed 200 J/hr, with ad traffic accounting for more than 87% of total overloaded overheads when the application is active, and analytics traffic dominating when the application becomes inactive. According to Pathak et al., the tested free apps (e.g., Angry Birds and Chess Free) consume only 25-35% of the energy. The remaining energy is used for advertising-related activities, such as ad downloads, user information tracking and updates, and radio tail times. Similarly, Mohan et al.'s research found that mobile advertising consumes more than 65 percent of communications energy and 23 percent of total consumption (including CPU, display, and communications). In contrast, Wei et al. observed 50 to 100 percent more system calls occurring in free applications than in their paid applications, which can lead to reduced performance and increased battery consumption. For these reasons, Nicutar et al. are focused on optimizing technologies, such as having nearby users share their links with each other using wireless links, such as WiFI or Bluetooth, which have a shorter range and require less power. Kibbutz allows users to aggregate their traffic through a subset of the link for lower energy consumption and shorter RTTs, and provides users with a guarantee of fairness.
In addition to energy consumption, the regular transfer behavior of the ad library aggregates data consumption. For example, about 1% of users on a cellular network in Europe spend at least 2 MB/day on ad traffic. This behavior refreshes or re-downloads images, text files, and JavaScript code every few seconds. Similarly, Qian et al. found that A-A traffic utilized about 20 percent of total cellular data. Typically, AdMob has a refresh rate of between 12 and 120 seconds, with a default rate of about 60 seconds. For InMobi, the minimum refresh rate is 20 seconds, while TheMillennial Media (35) and MobClix (164) refresh every 15 seconds. Because the default tail time for a 3G cellular network, such as AT&T, can take up to 17 seconds, these short intervals prevent the smartphone's radio from returning to IDLE. Also on 4GLTE and Wi-Fi networks, refresh rates make smartphone radios sleepless.
The above-mentioned problems are further exacerbated by the following three observations. The first is to repeatedly extract the same ads, with the first 100 ads rendered within 50% of the time. Popular ads can be downloaded up to 82 times on a single device. Second, about 37 per cent of advertising now continues to be available within 24 hours, before falling to 14 per cent in the following week. Third, the median for each ad is 15KB, and only a portion (5.8KB median) contains ad-specific components, such as ad HTML and images. For the third observation, the rest of the ad consists of redundant JavaScript. Similar redundancy has been found in the actual advertising HTML code content. Another study found that nearly 20 percent of total HTTP traffic was redundant. As a result, their research proposes a pre-take technology to reduce the energy and data consumption of mobile advertising.
To cut power consumption in half, AdCache uses pre-pick and cache technology and 20-second refresh intervals on 3G networks to move ads, such as static banners, animated banners, and text ads. Similarly, CAMEO, which predictively pre-picks mobile ads in bulk, uses cheap or free connections to support different ad selection models. By looking at 1.8M ads from 17K unique ads sent by AdMob in 10 countries, CAMEO showed that it could achieve 84% accuracy. In addition, when 100 ads are displayed, CAMEO is able to significantly reduce energy consumption by 25-37 times and bandwidth by a significant 4.8 times.
However, due to the limitations of advertising campaigns (e.g., budget and duration), pre-pick technology must also ensure SLA compliance and avoid loss of revenue. Thus, after assessing the energy costs of mobile advertising for the first 15 ad-supported Windows Phone applications, Mohan et al. implemented a mechanism for app usage forecasting and overbooking to model and optimize the relationship between pre-pick, energy consumption, SLA violations, and revenue loss. After studying the past behavior of users contained in two datasets, the researchers looked at two results. First, for mobile ads that expire within exactly 30 minutes of the service expiration date, using a statistical forecaster (i.e., the 80th percenteth-bit model) and a 20-minute forecast interval halves energy consumption while reducing SLA violations by at least 3 percent. Second, when the due date is longer, the 15-minute forecast interval is sufficient to satisfy the SLA. In addition, background traffic allows less energy to be consumed during this interval. Third, when the due date is short, the oversubscribed model used by the agent reduces SLA violations, but increases revenue losses.
SECTION IX.
Discussion
We now address some of the similarities and differences between web-based online advertising and in-app mobile advertising. We also highlight some of the potential trends and directions in academia and industry in digital advertising.
A. Online Advertising vs. MobileAdvertising
Web-based online advertising and in-app mobile advertising are two basic forms of digital advertising. However, they have many differences. Under.MobiAd [37], the differences include smaller ads, less storage access, and fewer handheld device download frequencies to compensate for smaller screen sizes, lower processing power, and less bandwidth. In fact, factors such as bandwidth and power usage are less important in online advertising. As a result, it receives little attention in the study of online advertising. But in mobile advertising, these factors are far from insignificant. In fact, bandwidth is determined by the connection. Although online ads are usually connectedWi-Fi /The computer on which the Ethernet connection is madeWebRendered on the browser, but the mobile ads we studied always appear on the connectionWi-Fi / CellularConnected to the application on the mobile device. As a result, ad traffic is different. Although the ad network uses client redirects in online advertising, server redirects are used in the mobile ecosystem to accommodate slower connections and limited data usage. SoCDNIt is also highly relevant in mobile ads[164]。 Because these devices are typically owned daily by their owners, human factors such as privacy issues are of greater importance in a mobile environment. Although extensive research has been conducted on the permissions of mobile devices, few people have solved the problem of browser permissions. For example, targeting technology may improve the efficiency of online advertising. On the security side, malicious ads, such as sneak downloads and click fraud, often appear in online ads, and ad-related malware in mobile apps is rare[149]。 Another difference is related to accessability. On the one hand, because online advertising must meetSOPTherefore, the ad network cannot access the data on the site.
Similarly, web browsers are completely isolated from other applications on the same computer. And while third-party network tracking may cover a shortage of information collection, it can also raise privacy concerns. Mobile ads outside of WebView6, on the other hand, are not currently subject to the separation of permissions provided by Web browsers. Because bundled ad libraries share the same set of permissions as host apps, ad networks can share user information within the app. In addition, access to persistent user identifiers (for example, IMEI, device identifiers, and location information) on mobile devices allows mobile tracking to extend beyond the boundaries of a single app. These methods allow ad networks to better target their customers; however, content-related ads created by Google AdSense allow ad networks to target customers based on content crawled from the pages they visit. Although crawling a page is relatively simple, you still can't get mobile ad content at runtime. As a result, new approaches are still being sought. At the same time, other technologies are destined to fade. Most smartphones do not support Flash advertising technology, so mobile ad developers must continue to adopt new technologies, such as HTML5, if they want to render media-rich mobile ads. Table XVII summarizes the differences we have witnessed.
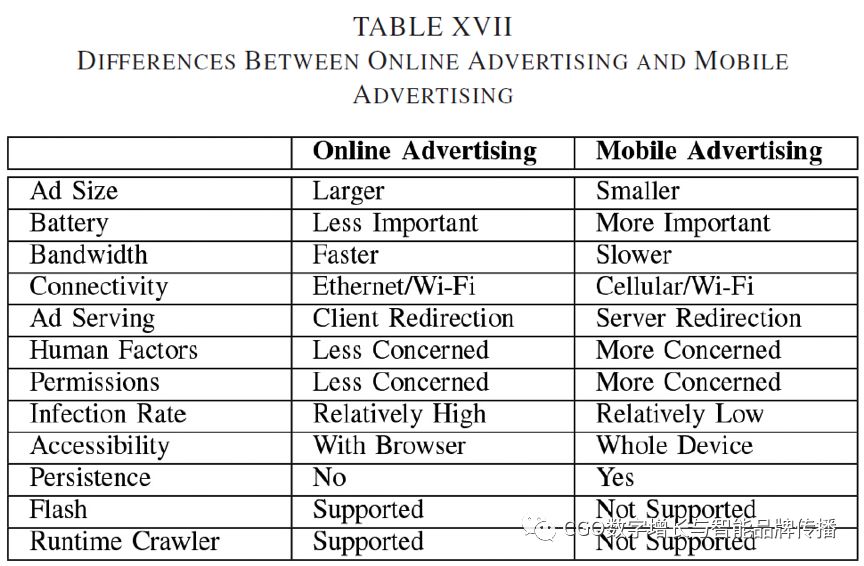
B. Potential directions for the industry, Potential Directions for Industry
The industry is actively and comprehensively working to improve the advertising experience for mobile users. Because rich media advertising varies in size and implementation[116]So.IABWork with major ad networks to provide definitions of mobile rich media advertising interfaces (MRAID)APIto unify many rich media ad formats. MeanwhileAppleAnd.GoogleCompanies such as companies are also working to standardize the use of advertising support internally. For example, since2013Years.5Month.1From now on,App StoreAccess is no longer acceptedUDIDnew app or app update[171]。 In a similar move,GoogleIn.2013Years.2Month fromGoogle PlayMore than was removed60,000applications[33]。 These low-quality applications typically contain ad libraries that require a lot of permissions[33]。 In a similar way, ad networks are changingSDKto blur the protection of intellectual property rights[23]。 For exampleAndroidDeletingACCESS_FINE_LOCATIONpermissions and cancellationsgetLastKnownLocation API[33]。 Because users may be annoyed by digital advertising,AdBlock Plusand other alternatives are now widely used. As a result, online advertisers like Google have begun paying ad blockers to get their permission to publish their ads[172]。
Because.Cameo[95]And.MobiAd[37]Such solutions require carrier involvement, and mobile network operators may exceed their advertisingAPImore involved in the advertising ecosystem. As for the underlying operating system,AndroidThe permission system still needs to make a number of changes.Google PlayApp permissions are grouped into related permission groups during installation, and they may contain both security and hazard permissions[173]。AndroidThe automatic update feature of may make the situation worse because existing applications can add new permissions without notifying the user[173]。 Such changes provide greater flexibility to the ad library and enable advertisers to better reach customers; At lastAndroidIt is also possible to adopt for new applicationsiOSStyle permission system[174]。 If so, we envision a more radical change in the advertising network.
C. Potential directions for the academic community, Potential Directions for Academia
We explored several key points in digital advertising and many contributions, including the technologies and applications of many researchers, to enhance the advertising ecosystem. We also note that online ad pre-pick technology is used to protect user privacy. For examplePrivadYou may need to cache near20MBdata related to advertising for daily use[30]。 In addition, in mobile advertising, pre-take can also be used to optimize energy consumption. Because.AdMobProvides up to48Hours of grace to get reports, so you can provide more flexibility to pre-pick ads. Another technique used to protect user privacy is permission separation. However, advertising providers and app developers are hesitant to apply it because of the risk of reducing advertising revenue. From.2015Beginning at the beginning of the year, the research community began to study ad targeting in mobile advertising[175],[176]。
Equally interesting is the new and diverse contribution of mobile advertising. For exampleAdNext [177]Provide users with highly relevant location-based ads by predicting their next visit based on their behavior history. In addition,AdTouch [178]Support is based onQRredirect of the landing page of the code. Finally, by consolidating in-app purchases, in-app mobile advertising can benefit users by reducing system modifications.
However, user privacy is still tracked without consent and unencrypted transmissions. In fact, users may dislike ads because they passively accept roles and then push for other improvements. Therefore, all parties, especially advertisers and users, will benefit from this design if users are allowed to make in-app purchases only by simply clicking on the target ad while voluntarily giving up private data. On the one hand, advertisers will meet their users' needs by sponsoring ads, and on the other hand, users will receive financial incentives by viewing ads. Finally, using secure channels for in-app purchases will result in protecting user privacy from eavesdropping.
Finally, as a pioneer of mobile advertising, the research of online advertising has been carried out for more than ten years. As a result, the research community has accumulated a large number of statistics. Research on the relevance of covering online and mobile advertising can further benefit the digital advertising sector.
SECTION X.
Conclusion
Digital advertising is now heavily integrated into many aspects of mobile devices. As a result, people who use smart devices for traditional online browsing and mobile applications have become an integral part of the digital advertising ecosystem. The ecosystem also includes ad brokers, publishers, advertisers and malicious agents. Therefore, users need to consider using their personal information (they trade for the service) as well as the power and data limitations of their devices. In addition, brokers and publishers seek to determine how best to monerate their work while meeting advertisers' needs without alienating their users. Advertisers also have a vested interest in targeting the right customers for their products to maximize their advertising investment. These goals create a unique relationship between all these participants. However, the ecosystem must also remain vigilant in its efforts to deter rogue agents who seek to compromise these relationships for malicious purposes.
With these issues in consideration, this survey aims to uncover many aspects of the advertising ecosystem, from advertising costs to privacy and malware issues. We also focus on in-app mobile advertising and online browsing on mobile devices, as these activities represent more and more users today. As mentioned earlier, there are now more60% of the video is viewed on a mobile device. Again, more than62% of mobile users use mobile devices to check email and access the Internet while99.5% of mobile user access to content[179]。 Social networks have also driven many changes in the way users interact with ads in mobile apps and online viewing.
In order to further understand the complexity of digital advertising, this paper explores the background and components of the advertising network. Some of them include advertisers, ad networks, publisher and user relationships, CPC goals, bidding and privacy protection. In addition, malicious advertising and related safeguards remain challenges for researchers. Some studies include mobile system features, mobile operating systems, and better security for ad libraries. In addition, continue to explore the unique limitations of power and data to reduce unnecessary network traffic, save valuable mobile power, and reduce unnecessary financial expenses for mobile users.
Equally important are tracking and analytics restrictions on mobile devices for targeted advertising and user protection. The fact that mobile devices are often targeted with their users leads to greater privacy issues. Of course, these issues lead to higher security requirements - and then policy changes to address them are added to the advertising ecosystem. To improve security, you need to pay more attention to application permissions and library bundles. Similarly, you need to provide users with better notifications about what permissions are granted to mobile application developers. Again, most apps on Google Play require users to give 3 to 15 permissions. As a result, more options are needed for users to return so many requests for their privacy.
Because ad networks are also interested in topics that users are willing to tolerate, these issues are of considerable importance to their business models. Several of the surveys discussed in this article provide recommendations for ad networks and publishers. By focusing on such literature and user preferences and policies, ad networks can further develop their business models and tracking technologies to improve marketing, security, and privacy protection. Therefore, researchers (academics and industry) must continue to identify new incentives that help drive and drive the advertising ecosystem. So every advance in controlling permissions, protecting privacy, and limiting the application of malware brings us closer to an appropriately balanced advertising ecosystem while measuring and exploiting user interests.
Bibliography
1.L. Goldberg, S. Silber, "At \$11.6billion in q1 2014 internet advertising revenues hit all-time first quarterhigh", Jun. 2014.
2.L. Goldberg, S. Silber, "Q3 2014internet advertising revenues hit \$12.4 billion making it the highest quarteron record", Dec. 2014.
3.G. Dunn, Cyber-Security and DataPrivacy Outlook and Review, 2013.
4.V. Dave, S. Guha, Y. Zhang, "ViceROI:Catching click-spam in search ad networks", Proc. ACM SIGSAC Conf.Comput. Commun. Secur., pp. 765-776, 2013.
5.Y. Wang, D. Burgener, A. Kuzmanovic, G.Maciá-Fernández, "Understanding the network and user-targeting propertiesof web advertising networks", Proc. 31st Int. Conf. Distrib.Comput. Syst. (ICDCS), pp. 613-622, 2011.
6.S. Muthukrishnan, "Ad Exchanges:Research Issues" in Proc. Internet Netw. Econ., pp. 1-12, 2009.
7. R. Gomes, V. Mirrokni, "Optimalrevenue-sharing double auctions with applications to ad exchanges", Proc.23rd Int. Conf. World Wide Web, pp. 19-28, 2014.
8.B. Stone-Gross, R. Stevens, A. Zarras, R.Kemmerer, C. Kruegel, G. Vigna, "Understanding fraudulent activities inonline ad exchanges", Proc. ACM SIGCOMM Conf. Internet Meas. Conf.,pp. 279-294, 2011.
9.S. Angel, M. Walfish, "Verifiableauctions for online ad exchanges", Proc. ACM Conf. SIGCOMM(SIGCOMM13), pp. 195-206, 2013.
10.A. O. Insider, How Ad Serving Works,Aug. 2013.
...... (Slightly) if you need references, please leave a message in the background.
(All rights above belong to the author and publisher of the paper, IEEE, Communication Surveys and Guides, IEEE Communications Surveys and Tutorials, except for the right to translate the text,Volume: 18 , Issue: 3 , thirdquarter 2016 )
This translation indicates the source of the article:
https://ieeexplore.ieee.org/document/7390161
You can also apply for full pdf from the following researchgate academic website
https://www.researchgate.net/publication/291951379_In-Depth_Survey_of_Digital_Advertising_Technologies
Extend your reading of this number:
Theoretical Original: Rebuilding brand and consumer relationships, global digital (messaging) marketing growth
WFAP2025: Master Interview Series for Future Advertising Research (Match Mama also)
Go to "Discovery" - "Take a look" browse "Friends are watching"